1. Introduction
Internet of Things technologies show tremendous promise in enhancing quality of life for many. Significant innovations and advances are helping to propel the development of novel IoT systems. Cheap and readily available hardware components are crucial to ensuring continuous adoption of these exciting networks.
Creating operating systems that support both existing and emerging IoT devices while aligning with current communication standards and best practices will help guide future progress. However, enabling interoperability between diverse operating systems in a way that accommodates heterogeneous deployment scenarios is critical for widespread adoption [1].
IoT infrastructures must intelligently adapt to changing network conditions to achieve their full potential. In this survey, we explore the landscape of existing IoT operating systems and evolving hardware options. We also consider promising directions for ongoing research. Several peer-reviewed studies on IoT operating system management are discussed in relation to opportunities, barriers, and potential remedies. Network capabilities, deployment flexibility, and support for diverse IoT applications are some of the key factors to be addressed. Finally, our conclusions and recommendations aim to inform continued advancement of versatile, scalable, and user-friendly IoT platforms. The internet of things is at the center of the technological transformation. Combining unified technology is challenging. The 5th era of smart Internet of Things, operating systems, communication via the air, liaison from device to device, modern cellular networks, and Internet of Things resources are examples of current "millimeter wave" innovations. The next generation of the Internet of Things is made possible by research. The affordability and progress of Internet of Things technology have led to a rise in long-range connectivity and device accessibility [1].
2. Operational mechanisms and features
Establishing links with other devices to enable information exchange is the aim of Internet of Things devices. Developers may design and deploy the Internet of Things by joining networks of sensors thanks to IOT platforms. Taking seriously the raised areas and materials involved in contrasting the different Internet of Things communication protocols, such as Message Queue Telemetry Transport. Many research studies were conducted to support Internet of Things applications using various protocols [2].
Data from sensor readings acquired without the usage of Internet of Things platforms was analyzed for four distinct protocols. Finding the amount and contributing causes to latency was the main goal of the investigation. Researchers employed several of these platforms for specialized implementations, relying on the 'Message Queue Telemetry Transport' protocol and pre-built hardware kits.
The researchers did not use Internet of Things operating systems in their past medical and healthcare solutions. Portable processors with a non-current operating system provide a broad platform [2].
The present Internet of Things is strongly interconnected with current cyber and physical systems. Recent IOT systems could be described as a broadly networked network with nodes that can be controlled and linked remotely. Our focus will be on current IoT advancements and security challenges. Providing security in modern times. The Internet of Things has additional challenges compared to traditional systems due to existing limitations.
Our goal is to showcase the security properties, limitations, and risks associated with contemporary Internet of Things technology, as well as security solutions tailored to these critical safety concerns. While there has been research on privacy and protection in IoT systems, The figure 1 shows Internet of things, there has been no comprehensive discussion of security recently [3].
Fig. 1. The figure shows the Internet of things
3. Safety requirements and resource limitations
Recent IOTs devices, such as sensors, controllers, and self-driving vehicles, have limited resources and need power tasks accomplished in milliseconds. These devices also require time-based qualities, which are represented by deadlines. The system's value determines the worth of the outcomes produced by missing a specific deadline. If the value decreases rapidly, the system is called hard, such as nuclear power plants or antilock braking systems; if it declines gradually, it is considered soft, such as streaming multimedia or automated glass wipers.
Properties of the majority of recent Internet of Things nodes
The growing popularity of the Internet of Things (IoT) necessitates the use of power efficient nodes capable of connecting to real-world devices. While some devices may communicate wirelessly without requiring electricity, IoT nodes embedded in physical objects require a protocol that is particularly designed to overcome their intrinsic restrictions. These nodes must meet a number of special requirements, including low-power design, cost efficiency, and restricted memory capacity. As a result, low-power, low-cost IoT nodes running over a wide communication range are relatively prevalent [4].
4. Telecommunications traffic is merged
Classic current time systems often consist of numerous nodes operating independently, with limited communication and capabilities. The Internet of Things connects cyber and physical nodes through industrial communication networks, which typically interact via the internet. Current applications need triggering events based on specific information. A reliable communication connection with required service quality, quantity, and data processing requirements is crucial for allowing these applications [5].
The Internet of Things now includes traffic with varied levels of timeliness, availability, and capacity, making it more versatile. Priority traffic for secure and precise system operation, including sensors for closed-circuit control and real-time control orders in avionics, automobiles, and home security. Moderate priority traffic, such as airliners navigation systems, power substation system monitoring, electric vehicle-charging station communication messages, heating, water sprayers in stations, air conditioning, lighting devices, food cooking machines, etc., is essential for proper system operation but has some delays, tolerances, drops, etc. [6]. Traffic that does not rely on network towers for wireless connection is considered low priority in the system. Examples of such traffic include engineering activity power substations, multimedia content transmission in airplanes, and alerts exchanged between smart equipment within home premises. These towers provide mobile communication and data transfer across wide geographic areas, allowing them to efficiently address the various demands of different businesses and sectors. In reality, these network towers play an essential role in maintaining uninterrupted communication, which is critical for the unrestricted and flawless operation of many sectors [7].
5. Modern Techniques
The idea of combining newer and current data sets may not seem unique. In 2004, the term 'edge computing' was coined to describe a system that sends program instructions and associated information to the network's edge for increased efficiency and performance. In 2009, the notion of virtualizing computer resources in the Wi-Fi subsystem was introduced. The interest in moving computing resources to the network's edge emerged following the advent of 'fog computing' for the Internet of Things. Academics have used many terms to describe 'fog computing', including 'edge computing'.
This word, 'edge computing', was invented by the designer of cloudlets, who considered the usage of virtual computers. Cloudlets were originally created to act as a replacement for remote mobile apps that were previously hosted on faraway clouds. The major reason for the development of cloudlets was to allow apps to offload computationally heavy activities to local virtual machines on the same Wi-Fi network. Recent research and investigations have shown that fog computing is an essential component of the larger domain of 'edge computing'. Fog computing refers to the use of the cloud to complete network gateways, with cloudlets being an appropriate option when nearby server devices are available. Other publications cover 'Edge Computing of Multiple Accesses', a standard created by the European Institute of Standards and Telecommunications. This standard outlines how telecommunications carriers deliver virtualization-based computing services to customers using a programming application interface. Commercial equipment already incorporates the Internet of Things, edge computing, and fog computing. The current partnership between "Open Fog" and the European Institute of Standards of Telecommunications, however, disproves the notion that "edge computing of multiple accesses" is just another term for "fog." The 'Edge Computing of Different Obtains' strategy can help accelerate the introduction of 'fog computing'. Many studies refer to 'edge computing of multiple accesses' as a synonym for 'fog computing'. The European Institute of Standards of Telecommunications introduced 'Edge Computing of Multiple Accesses' as a telecommunications standard. It specifies the interface of programming applications for telecom companies to provide virtualized computing services to their clients based on expansion [8], Internet of Things A to Z: Technologies and Applications. John Wiley & Sons, United States, 113-124). Previously, 'fog' was also called mist computing'. Recent articles classify mist as a subcategory of fog. Mist emphasized the necessity to expand computer capabilities to the Internet of Things 'extreme edge'. Positioning devices can minimize communication latency between Internet of Things devices to milliseconds [9].
Essentially, the goal of 'mist computing' is to provide Internet of Things objects with the ability to identify themselves in terms of self-organization, self-management, and various self-means. As a consequence, Internet of Things devices will be able to operate continuously even if their internet connection is intermittent. Generally speaking, "mist" devices may sound similar to stationary or mobile web services, where application services are embedded into various low-resource devices, including sensors, actuators, and cell phones. However, 'mist' is concerned with self- recognition and condition awareness, enabling the remote distribution of dynamic software code to diverse devices based on state and environment changes. Similar to 'fog', it provides a foundation for flexible reconfiguration and program deployment [9].
Understanding that the 'fog' requires support from all of the connected technologies of 'edge computing' indicates that no one is capable of installing and regulating 'fog' without integrating the technologies of 'edge computing'.
6. Security assaults and risks for the recent Internet of Things
Recent Internet of Things systems face a range of threats, depending on the adversary's goals and technology. In a system constructed using a vendor model, one of the contributing vendors may be malignant. That possible untrustworthy vendor may incorporate a number of malicious functions into the system's responsibilities.
Furthermore, even if the contributing vendors are not malevolent, improper coding approaches may cause difficulties. In a networked system, the opponent may target the communication interfaces. Because most of these technologies lacked authentication, communication channels were easily fabricated and intercepted.
The methods of attacks on recent time strategy are classified depending on the control over computer processes and the functional purpose of the attack. Only one way to get control of a target system is to inject a malicious virus or malware or to utilize lawful code for nefarious objectives. Furthermore, because nodes in the modern Internet of Things can communicate across untrusted channels such as the internet, the system is vulnerable to network attacks [10].
Aside from the repeated tests of forcefully crashing the system, as part of the assaults on the subset channels, the adversary may surreptitiously connect to the system and get sensitive data. Attacks against subset channels rely on determining system characteristics such as memory use patterns, task scheduling, power consumption, and so on. That information might be used later by the attackers to launch new attacks. We will highlight the most prevalent attacks on modern IoT systems:
An integrity violation occurs when malicious code is introduced. A competent adversary is capable of gaining a position in the system.
For example, an adversary may introduce a malicious job that respects the system's recent promises in order to avoid discovery and harm one or more current recent works. The attacker may utilize that task to control sensors and alter the system's behavior in an undesirable way [10]. The loss of integrity via code injection attacks comprises transferring portions of instruction to a device, which are saved in memory by the receiving application. The attacker then manipulates unknown channels, such as subset channels, to make the victim more vulnerable in order to extract sensitive information from them. Because recent time tasks are executed by nodes in the Recent Time Internet of Things (RT IoT), these attacks are particularly effective against these systems due to their predictable behavior. The hackers get access to temperature, memory, power consumption, and time management likes and dislikes, which allows them to collect crucial information. The Internet of Things (IoT) is a valuable communication channel, but it also raises privacy and security concerns. Interference, falsification, and disruption of control and information flows are examples of communication threats.
Protecting against these risks is tough since it is difficult to distinguish between illegal and lawful communication traffic without sacrificing service quality [11].
Cryptographic protection measures are frequently employed to tackle communication risks; however, this might raise the engineering technology of wireless communication and necessitate scheduling changes. Cryptography procedures are extremely costly and constrained, particularly for stationary devices in the IoT.
Therefore, tackling these risks is critical for the security and privacy of IoT systems. Cryptography may not be the best solution for many Internets of Things (IoT) applications owing to resource constraints and severe timing constraints. A method for incorporating security features without changing existing jobs is offered. Nodes in IoT networks are vulnerable to service denial attacks, in which attackers manipulate recent tasks and deplete system resources. Distributed service denial attacks include a large number of rogue nodes targeting devices at the same time, especially when substantial activities are scheduled. This can compromise system integrity and privacy, especially when crucial processes are scheduled to start. Implementing security measures without disrupting existing functions is crucial for IoT devices. The current processes for defending general information technology or permanent systems do not account for the timeliness, resource restrictions, and safety of the Internet of Things. These procedures require considerable revisions to be adaptive. Our recent efforts may be unified to protect against service denial attacks.
To be effective, attackers must conduct investigations and plan their attacks. We will explain this as follows:
7. Strategies to defend against assaults on the modern Internet of Things
These approaches are often classified into two main categories:
- Solutions that require specific hardware support to provide security.
- Software-level solutions that require no adjustments.
The first step is to defend yourself with hardware.
The 'Simplex' construction allows for protection without compromising system safety. The term "simplex" refers to a popular current time structure. When a sophisticated controller with excellent performance is not available or isn't working correctly, a simple safety controller is used in its place [12].
The 'Simplex' approach attempts to guarantee that a system is safe even when it is controlled by a sophisticated controller.
Using a 'Simplex' structure for protection involves monitoring attributes including time, memory access, system call traces, and abnormalities. of an unreliable entity that is tasked with more complex tasks and vulnerable to less secure media, including networks, input and output channels, the internet, etc. Furthermore, although architectural modifications can enhance the security posture of Internet of Things nodes, they might not be appropriate for systems that employ connection-oriented transport components [12].
We will discuss several recently proposed approaches to enhance Internet of Things security without requiring hardware support:
To combat subset channel attacks, attackers can use timed attacks to estimate memory allocation behavior. Recent systems lack separation of distributed resources among diverse tasks, causing this issue [13]. The Internet of Things is based on a connection-focused transport service.
When the system transitions between jobs, there is some overlap. Understanding the constraints of safeguarding between jobs is crucial for preventing assaults on specific channels. Integrating security, the Internet of Things is being promoted through techniques that limit the number of jobs scheduled, implementing high-priority scheduling tools. The scheduler clears the distributed cache when switching from a project with high protection, which demands greater privacy, to a process with low protection, which is unprotected and largely harmed [13].
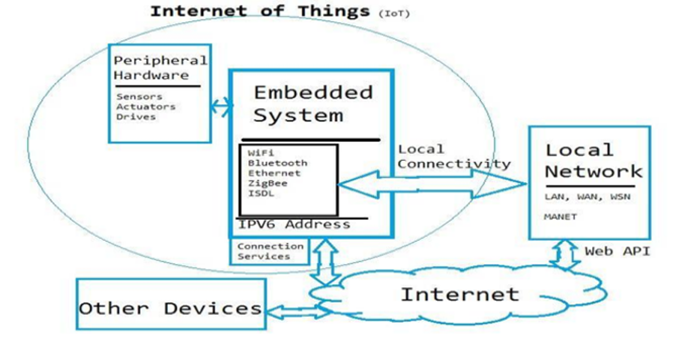
Fig. 2. A 'Simplex' structure for protection involves monitoring attributes including time, memory access, system call traces, and abnormalities
8. Suggested Use of the Internet of Things Platform
We created apps that include modern operating system features. Sensors, actuators, and communication modules make up the hardware layer. The Internet of Things system requires the following future sub-systems to be built:
- The Internet of Things server, which makes it easier for nodes to communicate with one another;
- The prototyping platform, which makes it possible to create Internet of Things nodes;
- The structure describes data exchange procedures, while the communication protocol governs message flow between Internet of Things nodes and the recent time server.
The suggested system offers dependable connections for a wide range of smart Internet of Things applications. The proposed Internet of Things platform utilizes the 'ARM Cortex-M4' processor, which is both energy-efficient and reliable. A smart phone is recommended as the Internet of Things node. The proposed architecture consists of critical servers and nodes for the Internet of Things. The key server facilitates communication between system nodes over the internet [13].
The system's proposed nodes are classified into four primary categories:
- 'Sensor' nodes detect their environment.
- 'Actuator' nodes that have an effect on their surroundings.
- 'Hybrid' nodes that perceive and influence their environment.
- Nodes designated as 'monitoring'.
The figure 3, depicts the potential structure of the system of the Internet of Things.
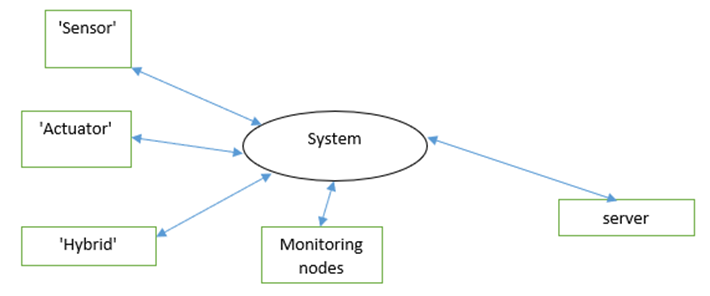
Fig. 3. Depicts the potential structure of the system of the Internet of Things
Below is a detailed explanation of the suggested system.
9. Suggested for IoT nodes
The proposed model is implemented using a "Nucleo Board" that uses the processor of the "ARM Cortex-M4"; this processor is specifically designed for great performance, low-power consumption, and low device prices, making it appropriate for the nodes of the Internet of Things. The suggested platform is a fixed system that could be designated for any controller types that meet the requirements of the system; it was developed, implemented, and successfully operated in the experiments. All nodes are made up of a few basic components, including a management unit that handles the node’s duties, Wi‑Fi hardware that enables wireless internet connectivity, sensors that collect data from the environment, and actuators that respond to this data [14].
System nodes are classified as 'Sensor', 'Actuator', 'Hybrid', and 'Monitoring' based on their connection to the key server. The 'Sensor' nodes perceive their surroundings and provide information to the server at regular intervals. These nodes have sensors but not actuators. The 'Actuator' nodes, with one or more actuators but no sensors, respond to monitoring node instructions and alter their environment [14].
The 'Hybrid' nodes integrate the capability of both actuator and sensor nodes. These nodes have both actuators and sensors. They interact with the Internet of Things server, send sensor data, and gather commands from monitoring nodes. The monitor nodes might be smartphones that regulate and monitor the system nodes. These nodes operate actuators and monitor sensor readings by issuing instructions and processing data, but do not include sensors or actuators themselves.
10. Server for Internet of things
The server is a crucial system component that enables communication between all nodes. It communicates with several nodes and provides monitoring nodes with sensor data [14].
Once a sensor node is recognized as a 'Sensor', the server sends data to registered monitors. Orders from monitoring nodes are sent to an actuator node by the server if it also serves as a monitoring node. The tasks of both nodes are managed by the server if a "hybrid" node doubles as a "monitoring" node. Orders are received, and sensor data is transmitted by the monitoring node [15].
The figure 4 depicts the flow of data over the server of the Internet of Things.
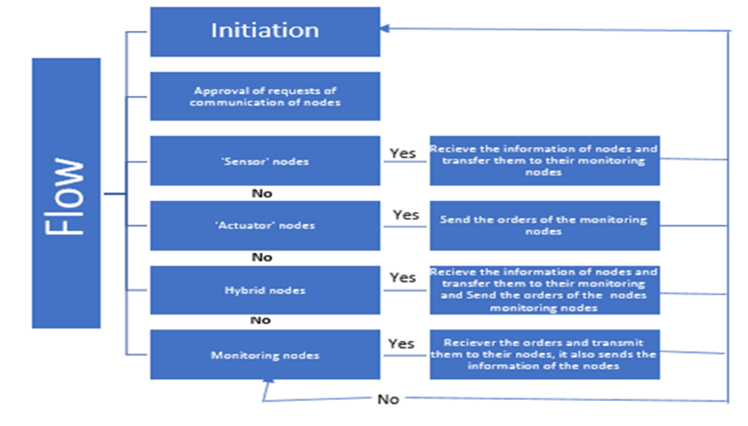
Fig. 4. Flow of data over the server of the Internet of Things
11. Suggested Communication Protocol
To accomplish these tasks, the system's nodes must communicate with one another through the key server. Each node connects to the key server by sending its identification and amount, and it waits for the server's acknowledgement before connecting to another node in the system.
The 'Sensor' node identifies itself and sends periodic information. The 'Actuator' node receives orders from the 'Monitoring' nodes via the key server. The 'Hybrid' node combines the functions of both the actuator and sensor nodes. After proof of identity, the 'Monitoring' node registers to receive data from specific sensor nodes and deliver instructions to defined actuator nodes.
Nodes communicate with the server by attempting to identify themselves and join.
Once acknowledged, they can successfully communicate with each other.
12. Establishment of the Test
Experiments are conducted to evaluate the effectiveness of the proposed communication technique and the 'Sending a message Queuing Telemetry Transport' protocol. Network settings are established to determine their impact on protocol performance [16].
The performance metrics assessed include the number of seconds of delay and the amount of data transferred per successfully sent message. The delay period refers to the time between message publication and server acknowledgement.
The setup consists of three machines: a laptop running a wide-area network emulator to simulate channel losses and communication delays, a personal computer serving as a server to facilitate communication between platforms, and a second laptop serving as a node for message publishing and acknowledgement. The server supports both protocols. A wide-area network emulation machine is used to send the messages to the server after the node publishes them. The node receives the server's acknowledgement via the emulation machine.
13. The experiment's outcomes
In the experiment with one node and one server, the two protocols were able to send their messages without worrying about the proportion of loss applied, indicating shows the two protocols have a suitable approach for message delivery when working with There are different rates of loss, therefore performance evaluations for message delay and the total quantity of data delivered for each message that was successfully sent. We created a safe method for digitally signing documents and certificates (MD5) utilizing the message digesting process.
Signatures for digital integrity and authentication documents [17, p. 50-55].
This article examines methods based on encoding time, decoding time, SMS size, power consumption, and throughput using a series of tests. The proposed strategy outperforms the comparison method, according to the results [18, p. 56-63].
Message latency is a crucial statistic, especially in modern systems where time is a key factor. Message delays can be attributed to loss rates and the need for retransmission. The 'Message Queuing Telemetry Transport' (MQTT) protocol with a specific service quality is compared to a communication protocol with a particular level of acknowledgment for comparable messages [16].
'Message Queuing Telemetry Transport' has a reduced packet size compared to the selected protocol, resulting in decreased message delay. See the figure 5.
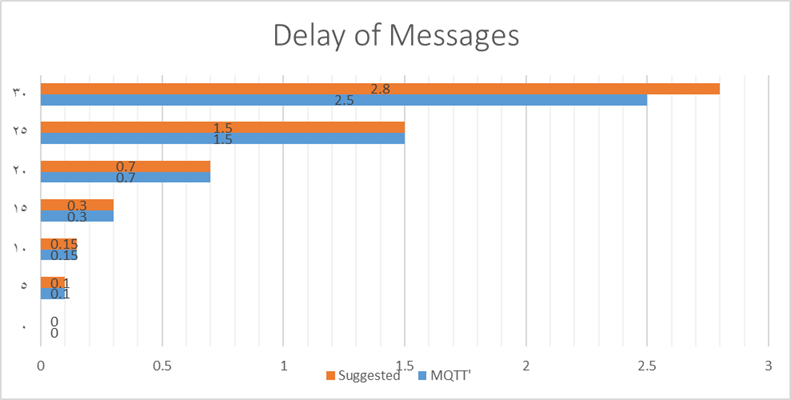
Fig. 5. 'Message Queuing Telemetry Transport' has a reduced packet size compared to the selected protocol, resulting in decreased message delay
14. Conclusions
The proliferation of smart gadgets such as cameras and home automation systems has resulted in the establishment of the 'Internet of Things', which connects previously disconnected objects and applications. However, the intricacy of assaults on these systems needs a reassessment of protective measures. This study intends to promote knowledge on modern time protection and to fill gaps in present protection systems.
The proposed approaches include hardware-assisted protection and no-adjustment protection. The study created an Internet of Things framework that acknowledges the intimate relationship between the past and the future.
15. Recommendations
I support merging Internet of Things systems into new technology. I recommend integrating Internet of Things systems with other technologies and expanding them use as they enable wireless data transmission across devices.
Furthermore, I support developing fresh approaches to protecting the privacy and security of Internet of Things data, as well as guarding against hacking and attacks; expanding safety resources is also essential.
Since I think my suggested model might be used for further study and discussion, I strongly advise paying attention to it. One can never obtain enough information on the enormous subject of the Internet of Things.
.png&w=384&q=75)
.png&w=640&q=75)