1. Introduction
Nowadays, the application of information technology to improve the quality of teaching and scientific research, enhancing efficiency in competition, operation, management and governance is an inevitable trend of universities. The competition between universities in the context of globalization, the expectation of learners and society, especially the remarkable development of science and technology in the fourth industrial revolution era has created change to future industries and human resource needs of professions. This revolution has been happening in three main areas: biotechnology, digital and physics. In particular, digital is one of the core areas of information technology, focusing mainly on: Artificial Intelligence (AI), Internet of Things (IoT) and Big Data. These pressures have forced universities to innovate comprehensively in developing strategy, teaching, learning, researching, management and governance. To do these, universities need to develop or modify a strategic plan, including a strategic information system planning (SISP).
An important issue in SISP is the information systems development guidelines at universities. To solve this issue, the authors have researched the documents, contacted and interviewed information technology experts from the universities in Hanoi, most of the experts' opinions refer to the construction of enterprise architecture.
Based on the development trend of technology, innovation requirements of universities, and the results of the research which includes surveys, interviews, consultation from experts, enterprise architecture frameworks which has been applied in practice by organizations, enterprises and universities and Vietnamese e-government architectural framework version 2.0, the authors have proposed applying and improving ITI-GAF to construct the enterprise architecture framework at Vietnam universities in the fourth industrial revolution era.
2. Literature review
Today, there are several definitions related to the Enterprise Architecture (EA) as follows: Federation of EA Professional Organizations (2013) defines EA as “a well-defined practice for conducting enterprise analysis, design, planning, and implementation, using a comprehensive approach at all times, for the successful development and execution of strategy. EA applies architecture principles and practices to guide organizations through the business, information, process, and technology changes necessary to execute their strategies. These practices utilize the various aspects of an enterprise to identify, motivate, and achieve these changes” [17].
The Gartner (2013) defines EA as a discipline: “EA is a discipline for proactively and holistically leading enterprise responses to disruptive forces by identifying and analyzing the execution of change toward desired business vision and outcomes. EA delivers value by presenting business and IT leaders with signature-ready recommendations for adjusting policies and projects to achieve target business outcomes that capitalize on relevant business disruptions. EA is used to steer decision making toward the evolution of the future state architecture” [4].
The EA Body of Knowledge (2014) defines EA as “analyzes areas of common activity within or between organizations, where information and other resources are exchanged to guide future states from an integrated viewpoint of strategy, business, and technology” [2].
Although there are several different definitions but EA usually consists of the following main components:
- The parts that make up the system itself.
- Relationship between departments and relationships with the external environment.
- Principles directing the design and development of those parts.
In terms of how it works, EA often specifies how information technology (IT) will support business processes. EA differs from IT architecture on the analytical level although it shares some of the design principles of the lower level architectures. The EA identifies the organization's core processes and how they will work together, how IT systems support processes, standard technical competencies, activities for all parts of the organization and guidelines to develop [7].
In terms of value, EA plays a key role in the building, reform and development of organizations. EA may not play its role clearly in the small organizations because all the resources and arising issues are insignificant in quantity, which is not difficult to control. However, when the organizations develop and scale up, the situation will change along with the increase of resources and the arise of many issues related to the process and business, thus easily causing overload and lost of control. Information systems (IS) have become complicated, difficult to control and the ability to respond is limited. One of the current inevitable trends is to apply EA approach and application in public agencies because it helps organizations synchronize IT with processes, business and mobilize synergy from different sources and departments, to avoid overlapping and duplicated investments, and to reduce investment time. In addition, due to a common set of standards for the entire system, the coordination and sharing of information among departments as well as system expansion is quite easy.
In terms of components, most EA’s have components as business architecture, information/data architecture, application architecture, technology architecture and information security architecture [11, 16].
In terms of process, according to Pearlson (2013), the process of building EA for organizations includes 04 steps [7] as follows:
- Step 1: Describe the current architecture through the process of surveying and evaluating the status of the system based on specific standards and criteria. From there, identify problems that exist in the current system.
- Step 2: Describe the future architecture of the organization to be achieved based on the architectural framework, the organization's vision, and the choice of technology.
- Step 3: Analyze the differences through the comparison of current and future architectures. They will be evidences to plan adjustments.
- Step 4: Build a transition plan through solutions, processes, priorities to move from current to future architecture.
According to ISO – Enterprise Architecture, there are about 57 architectural frameworks around the world. The most popular EAs are the TOGAF (The Open Group Architecture Framework), Zachman, FEAF (Federal Enterprise Architecture framework). In Vietnam, there is an ITI-GAF developed by the Institute of Information Technology - Hanoi National University [13].
- TOGAF is an architectural framework built by the Open Group organization. The purpose of the TOGAF is to assist in the design, evaluation, and development of EA. TOGAF provides a set of resources, an architectural perspective, while also allowing an architecture that guarantees its requirements. The basic characteristic of TOGAF is that it is not an EA but it is the methodology for EA building, so it is completely neutral and technology independent. The implementation of TOGAF is not dependent on and influenced by any specific technology platforms. The main components of TOGAF include: (1) Architectural development methods, (2) Guidelines and techniques for using architectural development methods, (3) Architectural content framework, (4) Warehouse architectural documents and organizational solutions, (5) Reference models, (6) Architectural competency framework [18-20].
- Zachman is an architectural framework developed by John Zachman in the 80s at IBM. It aims to provide a structure that categorizes and organizes the components of an organization. It gives conceptions of the architectural components of the organization and uses conceptual models of business, logical system model and engineering model at the demonstrated physical level in a table with rows and columns, made up of a matrix with 6 rows and 6 columns, where the rows are made up of looking at the system from a specific point of view, including: planner, scope, owner, designer, builder, subcontractor and Users. Each column describes the questions that every architectural element has to answer: what (What), how (How), where (Where), who (Who), when (When) and why (Why). Unlike the TOGAF, the Zachman architecture framework is not a methodology for building the architecture but only provides a methodology to describe the desired future architecture to be built [6, 7].
- FEAF is developed on the basis of the Zachman and TOGAF architecture framework, the main purpose of FEAF is to support the development and maintenance of unified, integrated, interagency architectures, and it focuses on evaluating the performance of IT investment. The FEAF builds on an integrated reference model and collaborative planning approach. The FEAF provides guidance processes for the development and maintenance of EAs. In particular, this process also supports the plan to move the model from present to future [15, 22, 23].
- ITI-GAF has been developed by the Information Technology Institute - Vietnam National University, Hanoi since 2009 based on EGIF (developed by a group of UNDP) and key features of the TOGAF framework. This architectural framework inherits the quintessence of EA, so it is possible to build a comprehensive and coherent EA, and at the same time, emphasize on simplicity, so it is suitable to the perception and level of IT application in developing countries and thus, it is easy to disseminate, propagate and guide the implementation and successful application in practice in Vietnam. Currently, the ITI-GAF framework has been used in a number of IT application projects of a number of ministries, sectors and localities in Vietnam [13, 14].
The above EA frameworks primarily describe how the organization works rather than how the technology is designed, so both the organization leadership and the IT leadership must work together inseparably. Today, all virtual business processes have been lumped into several components of IT, so the idea of tailoring IT to business processes has become irrelevant. Instead, business processes must be designed concurrently with information systems. In the context of the fourth industrial revolution, the EA frameworks remain important because they feature methodologies to build or describe the future EA in which the organization is expecting without depending on any technology platform. Therefore, they are not affected by changes in science and technology, but on the contrary, the development of science and technology will increase the success rate of implementing EA frameworks in practice.
3. Methodology
In this study, the authors use the following research methods: Document analysis and synthesis, modeling and qualitative research methods.
- Document analysis and synthesis method is mainly used when reviewing research, referenced documents including books, newspapers, magazines circulated by publishers, prestigious universities and domestic authorities. When analyzing and synthesizing documents, there are citations and evidences linking to specific references.
- Modeling method is used to describe architectural components in the EA framework, their flows and direction.
- Qualitative research method is used in the exploration and experienced sharing of information from technology experts. The total number of experts interviewed and shared experience is 36, including:
* Number of experts interviewed: 20 experts from 13 Vietnamese universities, including:
(1) 02 experts from Vietnam National University, Hanoi (VNU) (01 expert from Information Technology Institute and 01 expert from University of Engineering and Technology).
(2) 02 experts form Hanoi University of Science and Technology.
(3) 02 experts from National Economics University (01 expert sent an answer file through e-mail).
(4) 03 experts from Hanoi National University of Education.
(5) 01 expert from Posts and Telecommunications Institute of Technology.
(6) 01 expert from Electric Power University.
(7) 01 expert from Thuyloi University.
(8) 01 expert from Thuongmai University.
(9) 01 expert from National Academy of Public Administrationn.
(10) 01 expert from Education Management Academy.
(11) 01 expert from Banking Academy.
(12) 01 expert from Hanoi University of Natural Resources and Environment.
(13) 03 experts from Military Technology Academy (group interview)
* Number of experts shared experience: 16 experts, including:
(1) 01 expert from Hanoi Medical University.
(2) 15 experts shared experience in seminar which related to enterprise resource planning (ERP) system, e-Government architecture and information technology strategy (01 expert from Information and Communications Technology Department - Ministry of Education and Training, 11 experts from universities (University of Education - VNU, University of Engineering and Technology - VNU, Institute of Information Technology - VNU, Hanoi University of Science and Technology, Hanoi National University of Education), and 03 experts from Pyramid Software and Consulting (PSC)).
* Total questions interviewed: 22 questions related to strategic information system planning at universities, three of which questions related to the guidelines of strategic information system planning towards building enterprise architecture.
* Experts’ content of interviews and experience sharing are recorded through “Voice recorder” software of the Linfei Ltd. developer on IPhone. Subsequently, the authors have converted the recorded content into text by listening to the audio file through Windows Media software and dictating the content into Microsoft Word software. Particularly, the authors must hand-write when interviewed 03 experts from Military Technology Academy because experts asked the authors not to record. The identities of the experts are kept confidential. Data are synthesized and processed through Microsoft Excel and Nvivo software.
Results and discussion
After studying and analyzing the advantages and disadvantages of EA frameworks and refer to the regulation of e-Government architecture framework version 2.0, the authors propose to apply and improve ITI-GAF to build the EA framework at Vietnamese universities. The reason why the authors chose ITI-GAF rather than other EA frameworks is that ITI-GAF has been researched, applied, implemented and brought about some positive results at some universities, such as Vietnam National University, Hanoi and Hanoi University of Industry. The authors have also experimented with applying ITI-GAF in the EA framework construction of Hanoi National University of Education and obtained some encouraging results.
4.1. Results
Compared to traditional ITI-GAF [14] (fig. 1), the ITI-GAF proposed by the authors has inherited the advantages of the traditional ITI-GAF (simple, suitable, easier to deploy domestically than other EA frameworks), meeting the provisions of the Vietnamese Government Architecture Framework version 2.0. Specifically, the “Resources” component of the improved ITI-GAF have been more clarified than that of the traditional ITI-GAF on such sub-architectural components as business architecture, data architecture, application architecture, technology architecture, information architecture and information security architecture (fig. 2).
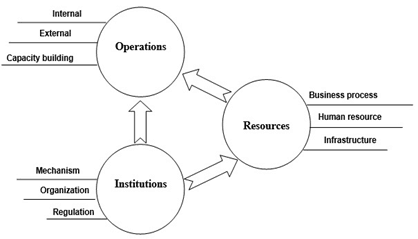
Fig. 1. Traditional ITI-GAF (Source: Nguyen Ai Viet at al. (2016))
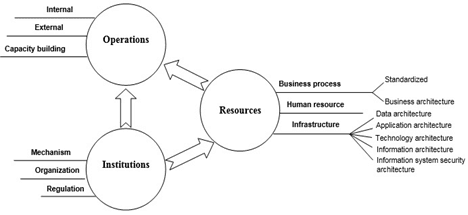
Fig. 2. Improved ITI-GAF (Source: The authors' proposal)
4.1.1. Institutions component
This component remains the same as the traditional ITI-GAF with mechanism, organization and regulation.
- Mechanism: Consists of practical actions based on information processing according to the business functions of the affiliated units of the universities.
- Organization: Including the definition of the roles and objectives of all positions and affiliated units of the universities and the relationships between them.
- Regulation: All rules defined in documents through different forms (Laws, Decrees, Circulars, Decisions ...).
4.1.2. Resources component
This component clarifies more about the business process, human resources and infrastructure of the universities.
4.1.2.1. Business process
All business processes of the universities will be designed based on ISO 9001: 2015 standards.
The main business processes will be mapping, implementation plan and organizational chart of the universities. Business architecture will include such components as professional management businesses, administrative procedural processes, data services, services support administrative procedures, business services support students, graduate students, PhD candidate, alumni, parents, employees, agencies, organizations and users (fig. 3).
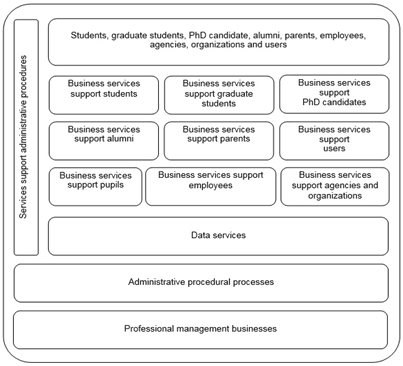
Fig. 3. Business Architecture
Sources: The authors' proposal was based on references from Vietnamese E-Government Architectural Framework version 2.0 (2019), E-Government Architecture of the Natural Resources and Environment Sector version 2.0 (2019), Regulations on the quality accreditation of higher education institutions (2017) and Instruction on the Teacher Education Institution Development Index (2020)
a) Professional management businesses are operations built and applied based on the reference and guidance of legal documents, specifically, Vietnam E-Government Architecture Framework version 2.0, E-Government Architecture of the Natural Resources and Environment Sector version 2.0, Regulations on the quality accreditation of higher education institutions and Instruction on the Teacher Education Institution Development Index [9, 11, 12, 21] as follows:
- Operations related to training as designing and management of training programs, design and manage schedules, scores management, degrees and certificates management, course and classes management, student management, practice management, time management...
- Operations related to science and technology such as research management, project management, scientific articles management; research time management...
- Operations related to finance such as financial reports, efficiency measure, accountant, public procurement, financial management, public fund management, asset management, payment, contract management.
- Operations related to human resource management such as employee training management, employee evaluation and classification, effective management, job positional management and organizational construction, benefit management and maintenance, recruitment, salary management, workforce downsizing management, human resources attraction and development.
- Other groups of operations such as document management, administration, international relationship, emulation - commendation, inspection and auditing, statistics - reports, evaluate quality of education, information manage, information and communication technology management, bidding management.
b) Administrative procedural processes are the processes built on the instructions of the legal documents. Processes can adjust to suit the actual situation.
c) Data services are independent services or support other business services and can be provided independently upon request.
d) Services support administrative procedures are services that support learners and related parties in implementing administrative procedures in accordance with regulations. For example: Services support payment researches, services support contract settlement procedures, information search services for scientific research and teaching hours, and research information search services.
e) Business services support students, graduate students, PhD candidate, alumni, parents, employees, agencies, organizations and users are services performed by administrative procedures in accordance with regulations. For example, business services for students include study plan consulting services, course selection, career guidance, startup and post-graduate support. This is the activity of management staff, lecturers, academic advisers in providing information about the specialized training, study roadmap and plan, how and conditions to select modules, warnings on academic results, career orientation, startup support and study plans to improve learners’ level after graduation. Advisory activities of staffs, lecturers and academic advisers have great importance to students and graduated students. This activity assists new students to familiarize themselves with the learning environment, reinforces confidence in career choices, early warning for learners to adjust their study plans, and provides recruitment information from employers so that graduate students can easily find jobs.
4.1.2.2. Human resources
Human resources in the universities include lecturers, staffs and employees. Human resources in the universities must master business skills and resources exploitative skills on the information system. In addition, they must be continuously trained to update knowledge through e-learning system.
4.1.2.3. Infrastructure
Infrastructure includes hardware, software, applications, data and databases, network systems, documents and technical solutions. They will support and improve the efficiency and effectiveness of all activities at universities. To describe present and future EA state of the technology infrastructure, designers must construct component architectures as data architecture, application architecture, technology architecture, information architecture and information security architecture.
4.1.2.3.1. Data architecture
Data architecture describes standards, physical data and logical structures of the system, data and database management software at universities. Data will be unified, shared, integrated and stored in data warehouses. In addition, data can query to support business. Databases will interconnect through a common database management system. Data and database system constructed base on technical regulations on data of higher education database system, Vietnamese E-Government Architecture Framework version 2.0 and E-Government Architecture of the Natural Resources and Environment Sector version 2.0 [8, 11, 12] (fig. 4).
- Business data warehouse serves daily access and business processing of departmental specialists. It serves as the main data warehouse.
- Reporting data warehouse contains data extracted from business data warehouse serving reporting, providing information and searching about universities activities.
- Backup data warehouse is responsible for backup data of business data warehouse.
- Information exchange data warehouse connects to enterprise service bus to share data, database with Ministry of Education and Training, the other ministries and universities.
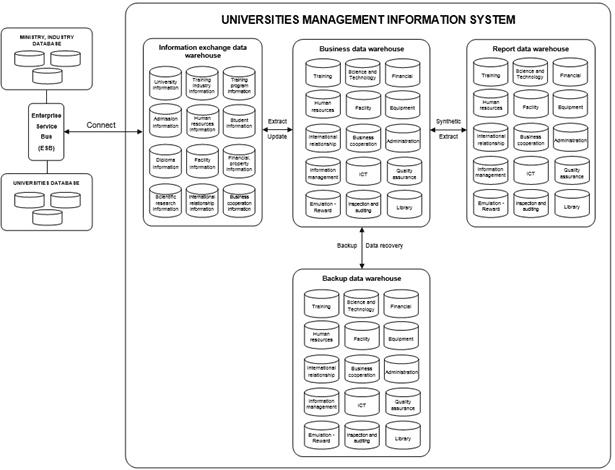
Fig. 4. Data Architecture
Sources: The authors' proposal was based on references from Vietnamese E-Government Architectural Framework version 2.0 (2019), E-Government Architecture of the Natural Resources and Environment Sector version 2.0 (2019) and the technical regulations on data of the system database system on higher education (2020)
4.1.2.3.2. Application Architecture
Application architecture describes the structure and interaction of applications to support the processes businesses, functions and manage universities’ information ownership. It gets 06 application layers: Access channels, web portal, list of applications and information systems, shared services, applications for data and applications for the information system infrastructure [3, 9, 11, 12, 21] (fig. 5).
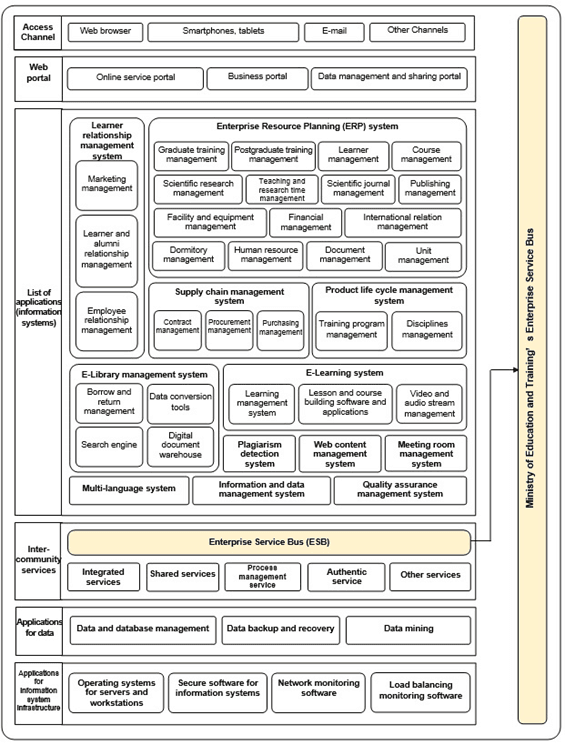
Fig. 5. Application Architecture
Sources: The authors' proposal was based on references from Vietnamese E-Government Architectural Framework version 2.0 (2019), E-Government Architecture of the Natural Resources and Environment Sector version 2.0 (2019), Kurt Hoffmann and Diane Freiberger (2017), Regulations on the quality accreditation of higher education institutions (2017) and Instruction on the Teacher Education Institution Development Index (2020)
a) Access channels: This layer includes applications to help the system exchange and interact with different users through web browsers, smartphones, tablets, email and the other access channels such as social networks.
b) Web portal: This layer gets online service portal used to assist users in searching universities’ related information, such as public information, courses information. The business portal provides business services to Web portal and functions support business processing of the universities’ units. The data management and sharing portal provides contents relate to data management and sharing on the Web portal.
c) List of applications (information systems): This layer includes 12 cores information systems as follows:
(1) Learner relationship management system. This system must have such modules as marketing management, learner and alumni relationship management, employee relationship management.
(2) Enterprise resource planning (ERP) system. This system must modules as graduate training management, postgraduate training management, learner management, course management, scientific research management, teaching and research time management, scientific journal management, publishing management, facility and equipment management, financial management, international relation management, dormitory management, human resource management, document management and unit management. Moreover, the system can add several functions such as scholarship management, internship management.
(3) Supply chain management system. This system must have such modules as contract management, procurement management and purchasing management.
(4) Product life cycle management system. This system must have such modules as training program management and disciplines management.
(5) E-Library management system. This system must have such modules as borrow and return management, data conversion tools, search engine and digital document warehouse.
(6) E-Learning management system. This system must include learning management system, lesson and course building software and applications, video and audio stream management system.
(7) Plagiarism detection system.
(8) Web content management system.
(9) Information and data management system.
(10) Meeting room management system.
(11) Multi-language system.
(12) Quality assurance management system.
d) Intercommunity services: This layer includes integrated services, shared services, process management service, authentic service and other services. It provided, exploited through enterprise service bus of the Ministry of Education and Training.
e) Applications for data: This layer includes software, applications for data and database management, data backup and recovery, data mining.
f) Applications for the information system infrastructure: This layer includes the operating systems for servers and workstations, secure software for information system, network-monitoring software and load balancing monitoring software.
4.1.2.3.3. Technology architecture
Technology architecture describes technologies to meet the requirements of business architecture, data architecture, application architecture and information architecture of universities. In the context of Industry 4.0, the authors proposes the core technologies for the universities’ EA as in figure 6 [11, 12].
a) Access Channel: Access channel uses technologies as mobile, internet of things, e-mail and other access technologies.
- Mobile technology applies to assist learners and stakeholders in accessing services supplied via web platforms through smartphones and tablets.
- Internet of things technology applies to collect information about the needs of learners and stakeholders, the quality of training and scientific research, this technology is a catalyst for business models to respond to interaction requirements in real time.
- E-mail technology applies to exchange information between universities and learners, organizations, other universities and stakeholder.
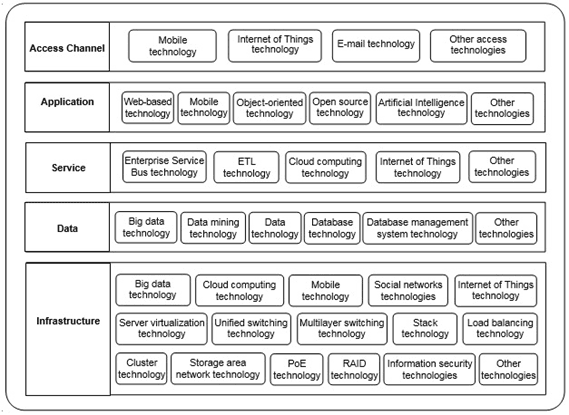
Fig. 6. Technology Architecture
Sources: The authors' proposal was based on references from Vietnamese E-Government Architectural Framework version 2.0 (2019), E-Government Architecture of the Natural Resources and Environment Sector version 2.0 (2019)
b) Application layer: This layer uses such technologies as web-based, mobile, object-oriented, open source, artificial intelligence and other technologies as image analysis technology, intelligent sound technology, image compression technology, and intelligent image recognition technology.
- Web-based technology applies to communicate and exchange with domestic and foreign information systems.
- Object-oriented technology applies to find out behavior of the data, making independent services that connect each other.
- Open source technology applies to expand and develop when there are business changes. In addition, it is continuously updated by open communities.
- Artificial intelligence technology applies to automate teaching, exam designing and scoring, monitoring and evaluation, administration and operation, and business and career consulting.
c) Service layer: This layer uses such technologies as Enterprise Service Bus (ESB), Extract Transform Load (ETL), cloud computing, Internet of Things and other technologies.
- Enterprise Service Bus technology applies to integrate and share data between universities and Ministry of Education and Training.
- Extracts Transform Load technology applies to extract, transform and load data from source databases to target databases. Furthermore, it also optimizes the purpose of using business data to construct useful information for universities’ strategic planning.
- Cloud computing technology applies to provide services to users and customers through applications on the internet.
- Internet of Things technology applies to collect information about the needs of learners and stakeholder.
d) Data layer: This layer uses technologies such as big data, data mining, data, database, database management system and other technologies.
- Big data technology applies to collect, analyze and process big data in real time, support decision making, provide processed and standardized data for the other data services, allow users choose data and supply data mining services.
- Data mining technology applies to classify data, find out the difference and similarity between the data, identify similar trends in transaction data, and predicting a future event.
- Data technology applies to analysis and improve business operates.
- Database technology applies to manage unstructured data.
- Database management system technology applies to manage structured data, standardize data and query with Structured Query Language (SQL) command.
e) Infrastructure: This layer uses such technologies as big data, cloud computing, mobile, social networks, Internet of things, server virtualization, unified switching, multilayer switching, stack, load balancing, cluster, storage area network (SAN), power over Ethernet (PoE), redundant array of independent disks (RAID), information security and other technologies. The authors do not reiterate big data, cloud computing, mobile, IoT technologies because they described above.
- Social network technology applies to exchange information between universities and social networks, supply information to learners and stakeholders via social networks and collect users’ data exploitive behaviors, habits.
- Server virtualization technology applies to share the resources of a physical server such as CPU, RAM, hard drive... and other resources.
- Unified switching technology applies to reduce the cost of investment in power and cooling systems for the data center, cabling system. Besides, it reduces connection ports and adapters on servers.
- Multilayer switching technology applies to process and transport large amounts of data, and finds the fastest route with extremely small latency in the network to meet the needs of users.
- Stack technology applies to combine multiple physical switches into one logical switch. This enhances the capability to debug, configures and manages physical switches as a single entity with a single IP address.
- Load balancing technology applies to distribute evenly of traffic between servers with the same function in a system. This will help the system reduce overload and crashes on servers, and improve the overall performance of the server system.
- Cluster technology applies to connect server with others in a parallel type and use it as a unified resource. If a server stops working due to issues, the whole work of this server will automatically switch to another server without causing system operation interrupt.
- SAN technology applies to transfer, share data between servers and storage devices. This technology helps to reduce risks to data, recover data if something goes wrong and has high data security.
- PoE technology applies to install switches, wireless access points without having to connect to electric power.
- RAID technology applies to combine hard disk drives (HDD) into a single HDD with aim guarantee data security and performance enhancements for servers.
- Information security technologies apply to limit risks for information, data and prevent malware, virus, spyware...
4.1.2.3.4. Information architecture
Information architecture describes information management strategic framework on universities’ websites with information organization principles, action planning and deployment of information management strategy [1, 11, 12] (fig. 7).
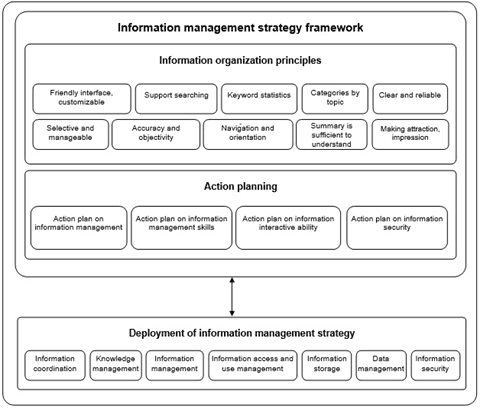
Fig. 7. Information Architecture
Sources: The authors' proposal was based on references from Vietnamese E-Government Architectural Framework version 2.0 (2019), E-Government Architecture of the Natural Resources and Environment Sector version 2.0 (2019), and Dan Brown (2010)
a) Information organization principles include:
- Friendly and customizable interface.
- Support searching for information.
- There are keyword statistics.
- There are categories by topic.
- Clear and reliable information.
- Information is selective and manageable.
- Information ensures accuracy and objectivity.
- There is information navigation and orientation.
- The summary information is sufficient to understand.
- Making attraction and impression for readers so they can remember, understand, and find information quickly and easily.
b) Action planning: Universities’ leaders direct and administer information in accordance with regulations with action plan on information management, action plan on information management skills, action plan on information interactive ability and action plan on information security.
c) Deploying information management strategy: This work will be deployed based on the information management strategy framework and focus on issues such as information coordination, knowledge management, information management, information access and use management, information storage, data management and information security.
4.1.2.3.5. Information security architecture
Information security architecture must meet technical and managerial requirements according to regulations issued by the Ministry of Information and Communications, and university quality accreditation standards and criteria [5, 9, 10, 21] (fig. 8).
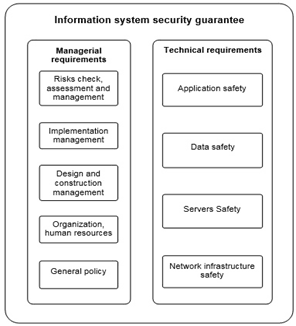
Fig. 8. Information Security Architecture
Sources: The authors' proposal was based on references from Vietnamese E-Government Architectural Framework version 2.0 (2019) and Regulations on ensuring safety of information system by level (2017), Regulations on the quality accreditation of higher education institutions (2017) and Instruction on the Teacher Education Institution Development Index (2020)
a) Managerial requirements: Focus on issues as general policy, organization, human resources, design and construction management, implementation management, risks check, assessment and management.
- General policy: There is an information security policy for users, including the content accessing and using the network, Internet resources and applications. Information security policy for system administrators and operators includes safety management of network infrastructure, server safety, application and data safety.
- Organization, human resources: There are processes and procedures for supplying and removing accounts, access rights of employees.
- Design and construction management: There are design documents and descriptions of options for ensuring the security of information systems. The plans for checking and verifying the system is implemented in accordance with the design documents and information security requirements before acceptance and handover. Level file is assessed and approved by the information security specialized unit.
- Implementation management: There is a process of managing and implementing the system in accordance with basic technical requirements, managing changes and moving the system, terminating operation, exploiting, liquidating and canceling the system. There is a plan for incident response in secure incident situation.
- Risks check, assessment and management: There is a plan every 2 years or irregularly when necessary to check, assess information security and manage information security risks. This work is performed by the information security specialized unit.
b) Technical requirements: Focus on such issues as network infrastructure safety, server safety, data safety and application safety.
- Network infrastructure safety: Network divides into subnet masks, each computer and device has individual internet protocol (IP) address. Firewall installs between internal network areas and Internet to prevent unauthorized access. Wireless networks have authentication and encryption mechanisms. Important network devices has authentication administrator account. Remote devices administration has protocols that support encryption.
- Server safety: All servers are installed anti-malware and anti-virus software, which are automatically and regularly updated. The password authentication mechanism ensures complexly, changes periodically and has a password scanning prevention mechanism. Authentication information is stored on the system in encrypted form. Disable default or inactive accounts on the system and unused services and software on servers. There are system logs for administrating and accessing servers. There are vulnerability patch mechanisms in the operating system and system services on servers.
- Data safety: Using independent storage systems to backup important data on the servers periodically.
- Application safety: Set passwords on the application with enough complexity to limit password detection attacks. Authentic information are stored in encrypted form. Setting access log writing, errors occurred. Do not use unencrypted network connections in remote application administration.
4.1.3. Operations component
This component remains the same as in the traditional ITI-GAF, including: Internal operations, external communication and capacity building.
4.1.3.1. Internal operations
Internal operations of university are regular operations with coordination among officials, employees and learners at the university as follows:
- Administrative management, such as document management, task management, weekly schedule management, work plan management, report management as required, regular reports, and statistical reports.
- Resources management, such as human resource management, science and technology management, financial management, asset management, information system management, and library management.
- Supporting university’s operations, such as training management (enrollment, curriculum development, scheduling, organization teaching, monitoring - evaluating the teaching process, considering the grade and graduation), and student management (files, study results, scholarships, rewards or discipline, surveys student).
4.1.3.2. External communication
External communication of the university includes activities related to enrollment, learners, partners, organizations, educational institutions and media related events. External communications of the universities as follows:
- Admission communication, such as enrollment counseling, career orientation support, and admission announcement.
- Communicate with learners, such as providing information and guiding learners to apply for credit, pay tuition, receive scholarships, feedback from learners about the program, and lecturers.
- Communicate with partners, such as information exchange on cooperative training, collaborative research and signing bilateral cooperation agreements.
- Communicate with organizations, such as coordinating with organizations to advise students on jobs, organize job fairs and transfer technology.
- Communicate with the other educational university, such as exchange of experiences, business, profession and training association.
- Communication through media, such as promoting the image of the universities, organizing conferences, seminars...
- Capacity building for the university covers activities related to the construction and development of human resources, business process reengineering, upgrading and building new facilities, managing infrastructure Information system, allocate financial resources and seek investment from the other organizations.
4.2. Discuss
In addition to the results obtained, the authors found that there are still some unresolved issues, for instance: What are the critical success factors the university’s EA framework? What hypotheses are included in the university’s EA framework theory model? What is the relationship between the variables in the university’s EA framework theory model?
During the survey of experts at universities, some experts have comments on the use of cloud computing technology in storage, mining and sharing data of universities. They expressed concerns about the safety and security of data because the data is not located in the data center of the university but shows the inconsistency in that if they do not use this technology, universities cannot meet the digital transformation in the industrial 4.0. Furthermore, the expert said, “If you want to use the cloud computing platform, you must understand it well”.
Some other experts have the opinion that the construction of the universities’ EA framework is “very standard”, but in reality when it is deployed at their university, it is difficult to succeed because their universities’ affiliated units have used individual management softwares, these experts suggest to study integrating individual software rather than building a new university EA.
Some experts point out that implementing universities’ EA will be very difficult or face risks and failures due to the fearless and unwilling habits of departmental specialists despite the software used in their business was very backward.
Some experts lamented that the voice of the information technology department was not as weighty and important as the finance department, so their improvement proposals were not interested by leaders, making them discouraged and unwilling to propose to the leaders anymore... The authors hope the above issues will be resolved in the future.
5. Conclusions
The fourth industrial revolution has brought changes in all aspects of life, including economy, society, labor, production and education of all countries in the world. This is an opportunity but also a challenge for the education sector and the universities to fundamentally and comprehensively change the education. Based on the research results, the authors suggest applying improved ITI-GAF to solve the issues of building EA at Vietnamese universities. The authors hope that these results will be applied into the practice of universities to improve the quality of teaching, research and management, thereby contributing to a innovate Vietnamese education.

.png&w=640&q=75)