I. Introductions.
In the year 2022 recorded a total of 4240 phishing and impersonate attacks, an increase of 40% in comparison to the year 2021. Particularly in the third quarter of the year 2022, recorded a sudden increase in the number of fraudulent domain names 1.8 times compared to the same period in 2021. These attacks are increasingly sophisticated and difficult to recognize, typically such as: Fraud by forging brand messages (SMS Brand name); scam using the names subtitle domain to access, and you must use your phone to access the phishing website; create loan applications. The main victims of the attacks are users using bank cards, electronic wallet. Notably, we recorded the occurrence of victims who were users of use securities services, borrow money online. We record a scam campaign using fake identity messages (SMS Fake Brandname) works continuously and strongly throughout whole the year 2022; International money transfer fraud campaign (the second quarter in the year 2022); Loan scam campaign money online (the third and fourth quarters in the year 2022).
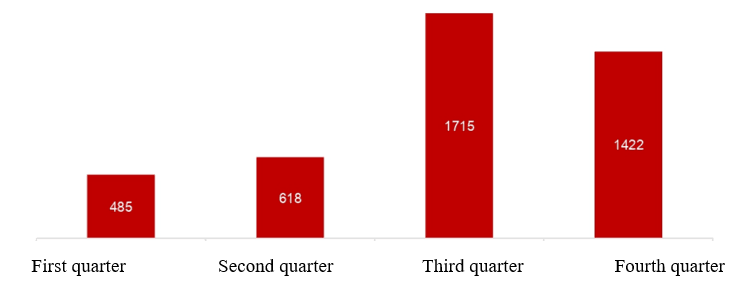
Fig. 1. Total Phishing and Impersonate attacks in 2022
The year 2022 also recorded a 13.9% increase in the total number of discovered and announced vulnerabilities compared to 2021. In which, there must be high-level and serious vulnerabilities on popular products and software on the Internet world including MS Exchange Server, WSO2, Atlassian Confluence, Zimbra, Oracle, Big-IP.... Worth it note that the Spring4Shell vulnerability in late March affects all released applications developed from the popular Spring Framework-framework in the world to develop Java applications. Gap also allows hackers to execute remote code similar to the critical Log4Shell vulnerability in December of the 2021 year. As can be seen, Java-related libraries, frameworks and products are still the preferred target of hackers and researchers. In addition, we also recorded the attack campaign exploits a 0-day vulnerability that allows remote code execution of Microsoft Exchange Server CVE-2022-41040 and CVE-2022-41082 (end of September 2022), this vulnerability exists until November 2022 to be patched. What’s worst is 150 million user account information for sale in cyberspace in 2022. Specifically, these information are stolen from many types of stolen malware. The most popular information today, fill in a picture like Redline Stealer. More seriously, login information of users into key systems of enterprises and organizations in Vietnam continuously appear in the data set and occupies a small part.
Leaked data is appearing more and more than in previous years and is for sale publicly. The reason is that the systems of businesses and organizations do not ensure information security, leading to exploited systems exploiting vulnerabilities, hackers gain access to internal systems and steal information. In addition, we also records leaks of organization's data and source code on online sharing platforms routes like: Github; The reason is that the software developers in the organization share the source code of the project to github for easy code management. We notified in 2022 has 29 data leaks in Vietnam affect large companies with millions of users, worth attention is the appearance of data leaks of units and companies such as build, civil engineering and develop products, software for businesses and organizations in the fields of finance, banking, and securities.
In addition, the trend of malicious code is active, typically the ransomware and stealer malware line is active again, strongly attacking the financial - service sector. Simultaneously, we recorded a number of new lines of malicious code that executes on multiple platforms and is difficult to analyze, with the goal of is cryptocurrency encryption, data collection, and digital currency mining. In 2022, there were also more than 10 million DDoS attacks with attack intensity more than 1G increasing quarterly, most notably the DDoS attack up to 140Gbps in July 2022. This warning about the protection and anti-DDoS attacks needs to be focused on to ensure the continuous operation of the network enterprise. It is also worth mentioning that in early May 2023, Google began providing the registration feature of new TLD (Top Level Domain) domains, including ZIP and MOV, such as test.zip, to store web pages or email addresses. Since these TLD domains were announced, there has been quite a bit of debate about whether they are safe and pose a cybersecurity risk to users. This is because ZIP and MOV are both legitimate file extensions, potentially misleading gullible users into visiting a malicious website instead of opening the file and accidentally downloading malware. This kind of phishing technique is called: “File Archiver In The Browser”. Security researcher nicknamed "mr.d0x" has developed a clever phishing toolkit that allows users to create fake versions of WinRar in the browser and Windows File Explorer that are displayed on domains. ZIP file to fool users into thinking they are opening a ZIP file.
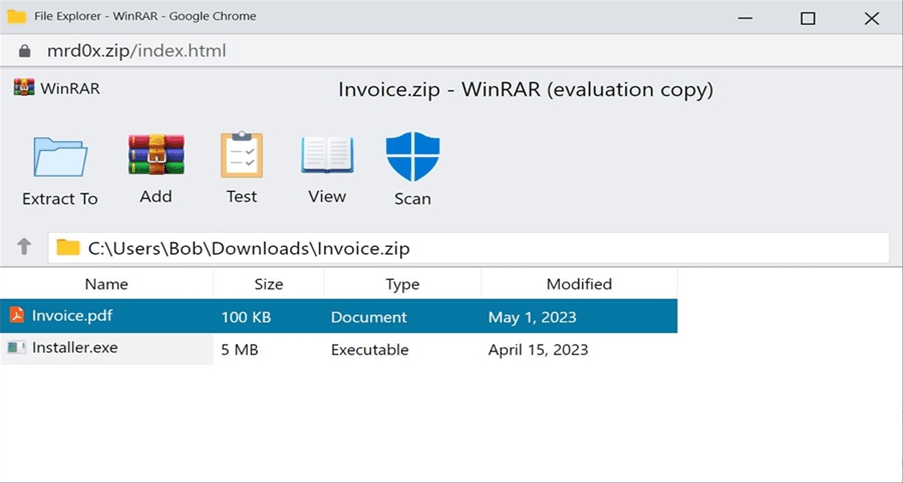
Fig. 2. Simulate WinRar in the browser
To make this fake WinRar window more convincing, the researchers implemented a dummy “Scan” button, which, when clicked, indicates that the files have been scanned and no links were detected any threat.
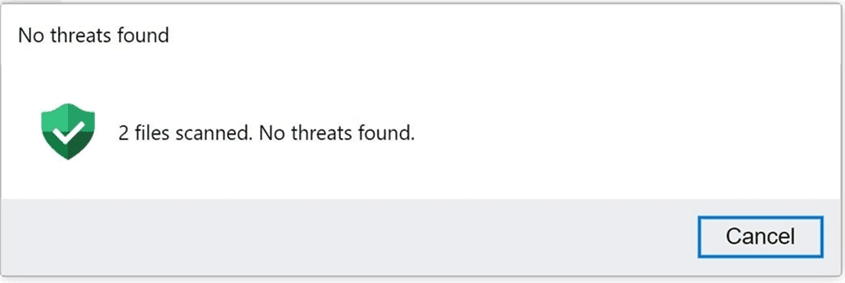
Fig. 3. Fake File Scanner
It's also worth mentioning that this phishing toolkit can be used for both credential theft and malware distribution. According to statistics of cybersecurity company Group-IB (Singapore), in 2022 there has been a 25% increase in the number of cases of using phishing toolkits, identifying 3,677 unique toolkits compared to 2021. Worthwhile Of particular interest is the growing trend of using Telegram to collect stolen data, with the rate nearly doubling from 5.6% in 2021 to 9.4% in 2022.
Due to the Gartner global spending on information security and risk management is about $ 160 billion in 2022, an increase of 7.2% compared to 2021. Development trends and growth in demand for Cloud security most clearly recorded, with the highest growth rate reaching 22.04% from 2021 to 2022. After that, Application security also recorded a growth of 21.28% in the period 2021-2022. The global information security market revenue is expected to reach 159.8 billion USD in 2022, with a share of for information security services, the market size is expected to reach 86.26 billion USD. Speed increase compound annual growth (CAGR) for the period 2022 - 2027 is about 13.33%, is expected to reach US$298.7 billion by 2020 -2027 (Statista, July 2022). In particular, the information security market in the ASEAN region reached CAGR 2015 - 2025 is about 17%. Three countries contribute significantly to this growth, including Singapore, Malaysia, Indonesia, are expected to account for 75% of the market by 2025. Indonesia, Philippines, Vietnam and Malaysia are predicted to be the fastest growing markets. (International Data Corporation, Gartner; A.T. Kearney analysis, 2021).
Table
(Unit: million dollars)
|
Group of products and services Growth |
2021 Year |
2022 Year |
Growth (%) |
|
Application Security |
4,962.5 |
6,018.3 |
21.28% |
|
Cloud Security |
4,322.8 |
5,275.7 |
22.04% |
|
Data Privacy |
1,140.1 |
1,263.6 |
10.83% |
|
Data Security |
3.1931 |
3,499.6 |
9.60% |
|
Identity Access Management |
15,865.0 |
18,019.3 |
13.58% |
|
Infrastructure Protection |
24,109.0 |
27,408.1 |
13.68% |
|
Integrated Risk Management |
5,647.4 |
6,220.6 |
10.15% |
|
Network Security Equipment |
17,558.0 |
19,076.4 |
8.65% |
|
Other Information Security Software |
1,767.4 |
2,031.8 |
14.96% |
|
Security Services |
71,081.0 |
71,684.0 |
0.85% |
|
Consumer Security Software |
8,103.3 |
8,658.9 |
6.86% |
|
Total |
157,749.7 |
169,156.2 |
7.23% |
Vietnam's information security market shows signs of stability, thanks to digital transformation activities in many areas. According to the report of the Ministry of Information and Communications of Vietnam government, revenue in the field of network security (including B2B and B2C) reached VND 3,319 billion (about 140 million US Dollars) in 2022 (it will reach VND 2,613 billion in 2021, up 27%). In which, the B2B market size in 2022 will reach about VND 2,300 billion. The number of employees in cyber security enterprises in 2022 is 3,452 people (an increase of about 10%, 3,138) in 2021.
Let's review the main information security trends in Vietnam in 2022
- The growing need to specialize in cloud translation by governments, businesses and organizations.
- Trends in compliance with information security policies.
In general, in 2022, the Information Security Law tends to tighten the technical standards of products and services, as well as promote enterprises in the information security industry, and at the same time strengthen supervision information systems from ministries, government agencies to businesses, especially in financial - banking sector (due to the increase in demand for payments and electronic transactions). Forecast in 2023, information safety documents will become more and more strict in terms of technical requirements as well as equipment information security products and services necessary for critical infrastructure. In addition, issues of electronic transactions will be more strictly regulated, leading to the development of risk, fraud, behavioral control, banking transactions, electronic transactions in Vietnam. The population database is managed by the agency government, but is expected to be shared with banks, which will further promote security issues population data. Information security awareness of individuals will have to increase more and more in the coming years. Therefore, the market of information security for broad-spectrum audiences also needs to be considered.
II. Information security trends in Vietnam in the near future
01. Data-centric Security trend
After the impact of the Covid-19 pandemic, in 2022, the demand for remote work will increase significantly, thereby requiring on information sharing, more data mining, data security is an inevitable consequence. A survey was carry out by Standard & Poor's found that 58% of respondents plan to increase targets for data security, with 16% planning a significant increase. Even with that investment, the number of daily data breaches increasing. The ubiquity of data and the complexity of the ways in which information is shared creates an environment a field for hackers to attack vulnerabilities and steal data. The protection of people's data is also promoted by the Government of Vietnam. The electronic identity subject is responsible for protecting protect electronic identity information; secure factor authentication. Service users need to comply with regulations technical standards for electronic identification and authentication. Manage and secure electronic identity account information, ensure the safe use of electronic identity accounts... At the same time comply with the provisions of the law on network information security, network security, electronic transactions, standards and technical regulations in the field of electronic authentication.
The activity of digitizing citizen data and using e-identifiers in Vietnam is increasing means that the need to protect user data of enterprise organizations is constantly expanding, especially distinguish groups with large volumes of data such as banks, insurance or government agencies, method... As users consume more data, database leaks also increase rapidly.
The impact of network data leaks has damaged many companies large and small, forcing them to step up network security to prevent future attacks.
02. Cloud security, specialized product lines for cloud, and integrated on the same platform
In Vietnam, the trend of businesses moving to the Cloud is considered to increase sharply in time especially since the beginning of the Covid-19 pandemic. Also at this stage, the influence of the chain global chip supply, leading to longer delivery times for hardware devices than before. Along with the development, besides, there are always baits that threaten data security, new forms. The network industry is also changing rapidly. According to Vietnam Cyberspace Security Technology JSC (VNCS), up to 84% of units participated in a survey for that traditional information security measures do not work well in the cloud environment. So, demand for specialized product lines cloud security is increasing strongly. The information security monitoring services on cloud infrastructure, security assessment of cloud infrastructure security... need to be focused and develop further.
03. The requirement to comply with international information security policy (Security Compliance) is increasing
The field of information security is becoming more and more important in Vietnam, targeting a key industry. According to the National Cybersecurity and Safety Strategy, proactively responding to challenges from cyberspace to 2025, with a vision to 2030 of the government, the strategy sets a goal to maintain and improve performance by 2030 the Vietnam's network safety and security ranking on global rankings; Vietnam has become one of Asia's leading cybersecurity and safety centers. Forming a market for safety and network security, with competition and influence in the whole region and the world, and maintaining the annual growth of 10 - 20 % per years in the revenue of the safety and network security market.... Therefore, compliance with international information security policy becomes an important factor to improve global competitiveness.
In the banking industry, the demand for compliance assessment with international standards is increasing after when the State bank promulgates regulations on the selection of compliant service providers international standards. At the end of March 2022, the PCI Security Standards Council (SSC), the organization that oversees the Payment Card Industry Data Security Standards (PCI DSS), announced the release of PCI DSS4.0 to replace the version 3.2.1, issued in 2018, expanded the regulatory criteria for Multi-factor Authentication (MFA) and passwords. Notable changes in this new version specifically include:
- Implement MFA for all access to cardholder data environments
- Replace the term “firewall” with “network security control” to support a variety of technologies more security.
- Increased flexibility for organizations to demonstrate how they are using other methods each other to achieve security goals;
- Adds targeted risk analytics to allow entities flexibility in determine how often they perform certain activities, in a way that best suits their business needs business and their level of risk.
04. Attack Surface risks due to moving to the cloud and working remotely, requiring solutions and features to control attack surface.
According to Gartner's forecast, the attack surface management market is in its infancy, but can serve as the foundation for the most effective enterprise information security plan in the world. near future. More and more organizations have encountered uncontrollable attack surfaces amid the COVID-19 pandemic and the widespread adoption of cloud services. According to statistics from Gartner, in 2022 just under 5% of attack surface management solutions are provided in information security platforms, however this number will increase to 70% by 2026.
The trend of moving to the cloud, integrating solutions on a single platform, the strong development of SaaS (Software as a Service), IoT (Internet of Things), OT (Operational Technology) has potential risks of unknown assets exposed to the internet. Therefore creating a large volume of demand for specialized solutions, featuring attack surface control (Attack Surface).
05. OT Security system for critical infrastructure
Due to the impact of the digital transformation revolution, technological devices began to be connected through the Internet IoT, and this creates an opportunity for attackers and hackers to infiltrate the system. In which the fields the major sectors affected by OT are aviation, energy, and logistics. In Vietnam, OT security is a very important challenge, in which: awareness of OT security is still limited, mainly concentrated in large energy enterprises; approaching the OT environment for testing and testing while still ensuring the system operational stability; OT security experts are limited in Vietnam. Companies that provide OT security monitoring services in Vietnam are not many, requiring a team of experienced experts and information security tools specifically for OT devices.
06. DevSecOps becomes a key business activity
DevSecOps (short for Development, Security and Operafions) aims to automate the integration of security at every stage of the software development lifecycle, or the “all components” mindset responsible for confidentiality”. DevSecOps integrates application security and infrastructure security one seamless way into Agile, DevOps tools and processes. It solves security problems when has just appeared with the advantages of fast, compact, easy and less expensive to repair. In addition, DevSecOps making application security and infrastructure security a shared responsibility of development, security, and operations teams, instead of, as in the past, being the sole responsibility of a separate security team. It enables “softer development, safer, earlier” by automating security delivery without slowing down the software development cycle.
A worldwide survey by Github with the participation of 4,300 companies and organizations that produce software, showed that the rate of DevSecOps adoption in software production has increased from 27% to 35.9% in just one year in 2021. This confirms, DevSecOps is and will continue to be the trend of information technology in the coming years. next year.
07. Cyber Supply-chain risk Management
According to a Gartner report in 2022, 89% of companies have experienced supply chain risks in the past 5 years, but the awareness of risks and plans to manage these risks of most companies are not yet really clear. Cyber supply-chain risks include: Risks from 3rd parties providing services, purchasing hardware devices, software infected with malicious code, risks when storing data from 3rd parties...
Therefore, solutions to assess and ensure information security for third parties (third-pary risk governance) are expected to be interested in the near future.
In addition to the trends mentioned above, there are also potential trends, such as:
+ Artificial Intelligence's Potential (AI)
AI, along with machine learning, has resulted in major gains in cybersecurity, with AI being applied across all market sectors. AI has played a crucial role in the development of automated security systems, natural language processing, face recognition, and autonomous threat detection. It's also being used to construct intelligent malware and attacks to get beyond the most up-to-date data security measures. Artificial intelligence-based threat detection systems can predict new attacks and notify administrators of data breaches instantly.
+ Integration and Automation
With the amount of data growing by the day, it is imperative that automation be used to provide more sophisticated data management. In today's challenging work climate, professionals and engineers are under increased pressure to deliver quick and effective solutions, making automation more helpful than ever. Security measurements are included in the agile process to build better secure software in every aspect. Larger, more complex online applications are much more difficult to safeguard, demanding incorporating automation and cyber security as core ideas in the software development process.
+ Ransomware with a Specific Target
Targeted ransomware is another critical cybersecurity problem that we can't seem to ignore. Industries, particularly in industrialized countries, rely largely on specialized software to manage their everyday operations. These ransomware targets are more targeted, such as the Wanna Cry ransomware assault on NHS hospitals in England and Scotland, which infected over 70,000 medical equipment. Though ransomware often threatens to reveal the victim's data unless a ransom is paid, it may also impact huge organizations or countries.

.png&w=640&q=75)