Introduction
In today's digital age, protecting sensitive and critical information from unauthorized access is paramount across all types of information systems, databases, and communication networks. Cryptographic protection is widely regarded as one of the most reliable methods for ensuring data security. Symmetric cryptographic algorithms, along with public key algorithms for key exchange and electronic digital signatures, are commonly used to secure sensitive information. These cryptographic methods have been extensively studied, discussed, and accepted by specialized cryptographic communities.
To ensure the effectiveness of these encryption methods, several factors must be carefully considered, including key length, processing speed, reliability, resistance to different types of attacks, computational resource consumption, and implementation costs. The key exchange process, in particular, plays a crucial role in the security of modern encryption systems. Moreover, with the advancement of personal computing power, modern devices are now equipped with secure processing capabilities, making them suitable for handling cryptographic protocols and key management securely [1, 2].
Public Key Infrastructure (PKI) is often used as a foundation for these encryption solutions, providing a framework for secure key management and digital signatures. However, it is essential that PKI implementations are resistant to compromise, loss, or malfunction of certification authorities. This research focuses on developing a robust and adaptable PKI system that can operate independently of potential vulnerabilities and ensure secure key management on personal computers. Additionally, the system has been audited by a third-party authority to address all critical security issues. The goal of this study is to modernize existing cryptographic solutions to meet the needs of evolving technologies and recommend their use in contemporary data transportation and communication systems.
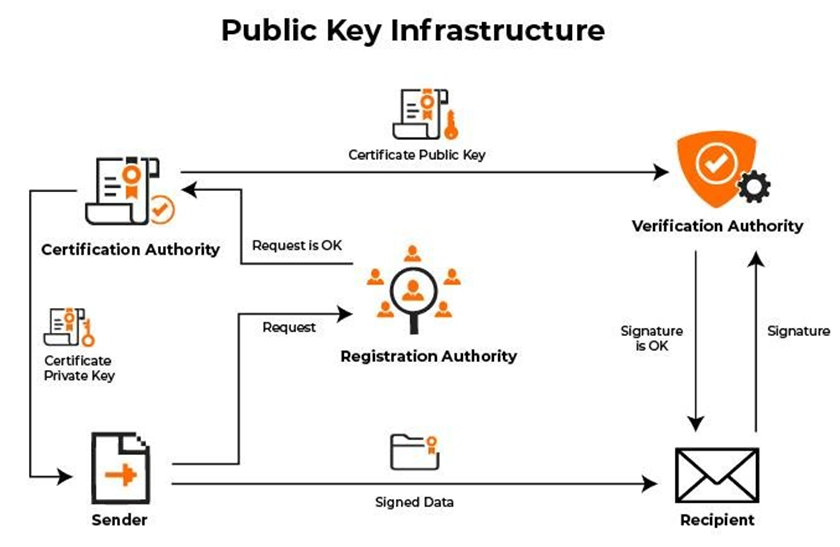
Fig. 1. Public Key Infrastructure Flowchart [11]
Background and Rationale
Governments increasingly depend on Information and Communication Technologies (ICT) in supporting their operations, which has greatly advanced the delivery of public services. Electronic access by the citizens of a country to forms and applications for key services, the ability to exercise and protect their rights online, and enablement of online financial transactions are the approaches being introduced by governments. With this transformation also comes a growing risk of breaches in data security if care is not taken: information has to be protected.
Government information systems are at great risk of being destroyed or of having information stored, modified, or processed without authorization. These systems may also be at risk of being stolen, encrypted, or sensitive information otherwise exposed by third parties. All this calls for robust encryption algorithms with strict controls over access on storage and processed data [3].
The primary objective of the study is critical evaluation and exposure of effective measures of sensitive information security in government systems with particular attention to modern methods of encryption. The paper provides an analysis of contemporary encryption technologies, their vulnerabilities, and best implementation practices within government systems. The study was developed using different analytical methods: synthesis, comparison, and the general scientific approach to the topic.
The research will have a special emphasis on the status of data protection in Russian government information systems. It will identify ways to lower the leaks of data and personal information that have to be protected. The research will evaluate modern encryption algorithms and their effectiveness in providing security for state information systems. The following are the basic tasks for the research:
- Identification of vulnerabilities and capabilities of potential attackers for ensuring integrity and confidentiality of data.
- Analysis of currently used data protection methods in government information systems.
- Development of a new encryption algorithm for government systems.
- Analyzing the results in detail to measure how effective the proposed solutions are.
Research Methods
This paper will be using multifaceted methods, both qualitative and quantitative, to evaluate information on contemporary techniques in cryptographic measures and strategies of data protection in government information systems. The paper is based on an analysis of encryption algorithms, key management systems, and regulatory frameworks. Addressed using a series of approaches combining analysis, synthesis, and comparison to satisfy the paper’s objectives. Namely, performing an extended assessment of symmetric and asymmetric cryptographic algorithms, focusing on identified vulnerabilities, computational efficiency, and applicability in use within government environments. Key management protocols are also given a critical appraisal in their contribution to system security. Data has been captured through a review of contemporary cryptographic literature, actual case studies on government implementations in encryption provided by leaders in standardizations of encryption techniques (such as NIST and FIPS).
The study also consists in developing a new encryption algorithm meant for governmental information systems. This algorithm, mimicking tests that happen through various kinds of attacks, checking threshold on consumed resources, and efficiency in terms of consumption of computational resources, should be tried out in veritably rigorous simulations. The obtained results are then subjected to comparative analysis for adequateness of the chosen alternative with respect to modern means. Apart from the technical part, the work is aimed at taking into consideration all the regulatory and compliance factors to make sure that the proposed solutions are in line with the legislative framework standardizing data protection of governmental data.
This multi-layered approach ensures a comprehensive evaluation of modern encryption technologies and provides actionable insights for improving data security in government systems.
Literature Review
The body of literature on encryption and data protection is extensive, with significant contributions from cryptography experts and institutions over the years. Key foundational works include Diffie and Hellman’s (1976) introduction of public-key cryptography, which laid the groundwork for asymmetric encryption methods like RSA, widely regarded as a breakthrough in secure communications [5]. Further developments in symmetric encryption, particularly the adoption of the Advanced Encryption Standard (AES), have been well-documented by the National Institute of Standards and Technology (NIST) . The transition from DES to AES addressed many of the vulnerabilities associated with earlier encryption methods, providing governments with a more secure option for data protection. Stallings’ "Cryptography and Network Security" offers a detailed overview of encryption protocols, focusing on their applicability in real-world scenarios, including government systems [6].
Emerging trends in encryption, such as quantum cryptography and homomorphic encryption, have also received increasing attention in the literature. Katz and Lindell’s "Introduction to Modern Cryptography" explores these new technologies and their potential to address future challenges in secure communication. Homomorphic encryption, for instance, is recognized for its ability to perform computations on encrypted data, a feature that could revolutionize secure data processing in government cloud environments. Meanwhile, literature on quantum encryption highlights the need for governments to develop quantum-safe encryption methods as the computational power of quantum computers threatens to break traditional encryption algorithms. Overall, the literature provides a solid foundation for analyzing the evolution of encryption methods, the regulatory landscape, and the future direction of cryptographic technologies in government systems.
Key Components of Encryption Systems
A comprehensive analysis of the fundamental components of modern cryptographic encryption systems is essential to understand how they protect data from unauthorized access. These components are the building blocks that enable the creation of secure software and hardware tools, designed to ensure confidentiality and integrity in information systems. By analyzing these elements, we can evaluate the quality, reliability, and potential effectiveness of custom-designed encryption systems for real-world applications in government databases and security systems.
One of the challenges in designing an ideal encryption algorithm is the difficulty of balancing theoretical security with practical implementation. It is not enough to develop secure encryption algorithms on paper; they must also perform efficiently in practice, minimizing vulnerabilities while ensuring robust protection. A structured approach to designing encryption systems is crucial to creating effective tools that meet the demands of modern data protection. The system's key components, which can function as standalone protection tools or as part of larger frameworks, ensure the confidentiality of sensitive information while being rigorously tested for computational performance [7].
Symmetric and Asymmetric Encryption
In symmetric encryption, the same key is used to both encrypt and decrypt data. This method is computationally efficient and ideal for encrypting large volumes of data [4]. However, the challenge lies in the secure distribution of the encryption key, as both parties must have access to the same key. The Data Encryption Standard (DES), once a widely used symmetric encryption algorithm, has been rendered obsolete due to its susceptibility to brute-force attacks by modern computers. Its successor, the Advanced Encryption Standard (AES), remains one of the most widely used encryption methods due to its stronger security and faster processing capabilities [5].
In contrast, asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. This method is more secure for transmitting data over unsecured channels, as the private key remains confidential. The RSA algorithm, one of the most widely used asymmetric encryption protocols, relies on the mathematical difficulty of factoring large prime numbers to ensure security [6]. While RSA offers enhanced security compared to symmetric encryption, it requires significantly more computational power, making it slower for encrypting large datasets. The use of elliptic curve cryptography (ECC), which provides similar levels of security with shorter key lengths, is an emerging trend in asymmetric cryptography, particularly for mobile and embedded systems [7].
Table 1
Comparison Table of Symmetric vs. Asymmetric Encryption Algorithms
| Characteristic | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Length | Typically shorter (128-256 bits) | Longer (1024-4096 bits) |
| Speed | Faster | Slower |
| Security Level | Good, but vulnerable if key is compromised | High, more secure even with compromised channel |
| Key Distribution | Challenging, requires secure key exchange | Easier, uses public/private key pairs |
Compliance Frameworks
In the realm of information security, particularly for government systems, a compliance framework is critical for ensuring adherence to security standards and preventing data breaches or unauthorized access. Such frameworks are designed to allocate resources effectively, ensure the enforcement of security requirements, and protect corporate and governmental data.
A key element of any compliance framework is the ability to assess whether information security measures comply with established policies. This involves the development of methodologies for evaluating the alignment of information systems with security protocols, ensuring that they meet compliance standards. However, a significant challenge lies in the automated collection and centralization of security data from a wide range of devices, including firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and antivirus software. Centralizing this data into a single, comprehensive view of network and workstation security can be difficult, particularly when different technologies are used across the system.
Additionally, the process of collecting, consolidating, and analyzing security events to provide actionable insights for compliance assessment remains a challenge. Disparate security technologies, which operate in isolation, complicate efforts to establish standardized protection policies. This fragmentation can hinder the development of unified incident response strategies, as well as the ability to effectively manage threats across the system.
Effective compliance management requires prioritizing security objectives and implementing action plans to mitigate risks. Automating key security management functions – such as software and hardware updates, threat notifications, and continuous network monitoring – is essential to maintaining compliance. The development of security policies within a compliance framework is often driven by a combination of business security drivers and threat models, each of which brings unique requirements. By establishing a comprehensive compliance framework, organizations can enhance their ability to respond to security incidents, protect sensitive data, and ensure that their systems meet both regulatory and internal security standards.
Challenges and Vulnerabilities in Government Encryption Systems
The successful operation of e-government systems and secure Internet-based services, such as e-commerce, heavily depends on the strength of their information security protocols. As cyber threats become more advanced, governments must continually update their electronic data protection tools and adapt to new security challenges. These challenges extend beyond technological vulnerabilities and include unfavorable political, economic, and environmental factors that can influence the effectiveness of encryption strategies.
One of the critical tasks for government systems is the ongoing classification and analysis of encrypted information to ensure it meets the stringent security requirements. The process involves defining standards for data protection, employing national cryptographic tools, and implementing procedures for encrypted data handling by government authorities. These standards provide a legal framework for how encryption tools should be deployed and managed, including detailed classifications of encryption levels and data erasure protocols. Government institutions must follow these established norms, which also allow for special requests, such as the review of encryption levels or the certification of data erasure methods for enhanced security.
However, one of the major challenges in government encryption systems is the slow pace of updating cryptographic standards. Governments often face significant obstacles in bringing certification procedures in line with the rapid advancements in cryptography. Without a modernized and adaptive certification process, even sophisticated encryption systems can be vulnerable to exploitation. This gap between regulatory standards and technological innovation underscores the need for ongoing research and collaboration between cryptography experts and security regulators to ensure that government systems remain secure against emerging threats.
Backdoor Controversies
Before 2013, there was a widespread belief that cryptographic methods, once deployed, were secure and immune to breaches. This confidence was shattered when revelations emerged that certain companies had entered into secret agreements to install backdoors in their encryption software. These backdoors allow for remote control and monitoring of encrypted communication, making it possible to intercept data transmitted via virtual private networks (VPNs) or other encrypted channels [9].
A backdoor enables unauthorized access by bypassing encryption protections and can compromise both the client and server systems. For example, in the case of closed-source encryption, an external entity with access to the backdoor can monitor, decrypt, and even manipulate communications without the knowledge of the users involved. This revelation fundamentally changed the way encryption is perceived. It became clear that security does not solely depend on the cryptographic algorithms themselves but also on the integrity of the organizations and individuals responsible for protecting the encryption keys. The presence of backdoors has undermined the trust in previously reliable encryption methods, compelling governments and security experts to rethink their approach to securing sensitive data.
Case Studies of Encryption Implementation in Government Systems
Russian Government Systems
In recent years, the Russian government has taken several important steps to improve the protection of personal and sensitive data through encryption. Notably, the approval of the cryptographic algorithm GOST R 34.10–2001 marked a significant development in government encryption practices. This algorithm, alongside GOST R 34.11–94 for data message digest duplication, was extensively tested and found to be highly resistant to decryption efforts up until 2015.
The Federal Security Service (FSB) of Russia continued to push for higher security standards, leading to the development and certification of the MDM GOST 34.10–2012 cryptographic module. This module offered enhanced encryption capabilities and addressed earlier vulnerabilities in government data protection systems. By 2016, the Russian Cryptography Institute had introduced further improvements with the Kuznyechik cryptographic algorithm, designed for automatic systems, and implemented AES in various encryption modes along with SHA3 encryption functions [10].
One notable requirement for the cryptographic equipment in use was its ability to operate in a hidden recovery mode for forbidden transformations. This feature provided the capability to restore encrypted data, even when such transformations were technically prohibited, ensuring that government agencies retained access to critical information in case of emergency. Through rigorous analysis and testing, these cryptographic modules have proven to be effective in safeguarding sensitive government data, ensuring robust protection against unauthorized access.
United States Government Systems
The U.S. government has developed specific standards and protocols for encryption in public information systems to ensure compliance with agency-specific regulations. These standards are designed to ensure the authenticity, availability, and confidentiality of information while protecting it throughout its lifecycle – from data creation and transmission to storage and maintenance.
Key principles of U.S. government encryption systems include integrity, anonymity, and availability. Integrity ensures that the data remains unaltered, while anonymity protects the identities of the users involved in communication. The standards also incorporate mechanisms to mitigate damage caused by breaches and to ensure secure and efficient transmission of information.
Encryption systems in the U.S. are also equipped to guard against traffic analysis – the process of intercepting and examining messages to deduce information from patterns of communication. To prevent this, secure communication channels are established, allowing the safe and timely exchange of information, especially in critical government functions.
Moreover, different encryption systems are used depending on the operational environment and the level of data sensitivity. For instance, government agencies handling classified information employ advanced encryption systems with multiple layers of physical protection to safeguard data from unauthorized access. The standards also address the management of cryptographic keys, ensuring that key generation, distribution, and destruction are conducted in a secure manner. This comprehensive approach to encryption ensures that U.S. government systems remain secure, even in the face of evolving cyber threats.
European Union Government Systems
Government information systems in European Union (EU) countries operate under the principles of a unified European telecommunications and data processing network. These systems are governed by operating agreements between EU member states, third countries, and other organizations, which establish the framework for the operation of this network. However, analysis of these documents reveals that the principles governing confidentiality and information integrity are often not explicitly defined in these agreements. Instead, they rely on references to international conventions, such as the EU Data Protection Convention.
Despite the existence of such conventions, the absence of a single, comprehensive multilateral agreement covering all EU countries means that there are inconsistencies in how data protection and information exchange are regulated across the region. This gap highlights the urgent need for international agreements that establish mutual recognition of compliance frameworks and uniform data protection rules across Europe. The European Economic Community (EEC) also lacks clear and detailed principles governing the confidentiality, integrity, and availability of information in government systems, further exacerbating the challenge of securing cross-border data flows.
Moreover, current agreements often fail to outline the necessary legal controls and fail to define the criteria for the level and nature of the security measures applied by telecommunication exchanges and data institutions. This lack of uniform regulation and the absence of detailed legal frameworks for data security present a significant challenge for the protection of sensitive government information across EU member states. To address these issues, there is a pressing need for a unified and consistent approach to information security regulations within the EU, ensuring that all member states adhere to the same high standards of data protection.
Table 2
Comparison of Encryption Standards between Russia, USA, and the EU
| Characteristic | Russia | USA | EU |
|---|---|---|---|
| Primary Encryption Standards | GOST R 34.10-2012, Kuznyechik | FIPS, NIST SP 800 series, AES, RSA | ETSI, ENISA standards, GDPR-compliant methods |
| Key Management Focus | Government-controlled key management, state-regulated cryptographic modules | PKI widely used, flexible key management systems | Focus on privacy and data protection, PKI systems |
| Compliance Framework | Highly centralized, regulated by FSB | NIST compliance, focus on commercial and military systems | GDPR enforcement, cross-border data protection rules |
| Government Control Over Encryption | Strict state control, mandatory certification for encryption tools | Moderate, with privacy laws like FISA for government oversight | Distributed control with national agencies, strong privacy regulations |
| Emerging Trends | Quantum encryption, national cryptographic tools | Quantum-safe cryptography, cloud-based encryption | Homomorphic encryption, secure data transmission for IoT |
Emerging Trends in Encryption Technologies
The future of cryptographic technology is poised for significant advancements across several key areas. One of the primary developments is the creation of new cryptographic algorithms and protocols designed to integrate encryption mechanisms into the rapidly expanding Internet of Things (IoT) ecosystem. As IoT devices continue to proliferate, the challenge of ensuring secure data transmission while maintaining resource efficiency is becoming increasingly important. Cryptographic protocols that are lightweight yet robust enough to safeguard the vast and constantly growing data sets generated by these devices are in development, focusing on scalability and energy-efficient implementations [9].
Another promising trend is the advancement of homomorphic encryption, which enables operations to be performed on encrypted data without first decrypting it. This breakthrough allows for secure computations in cloud environments and other data-sharing platforms while maintaining data privacy. While homomorphic encryption has great potential, practical implementation remains challenging due to the significant computational overhead involved in processing encrypted data. Research is ongoing to make homomorphic encryption more efficient, particularly in handling big data and IoT-generated data sets.
The imminent threat posed by quantum computing has sparked a global race to develop quantum-safe cryptographic algorithms. Quantum computers, once fully operational, could break traditional encryption methods such as RSA and ECC by leveraging their ability to perform complex calculations exponentially faster than classical computers. As a result, many countries are now investing in research and development of cryptographic solutions that can resist quantum attacks. National quantum technology programs are also being launched, aiming to integrate quantum cryptography into critical government systems.
The shift towards quantum-resistant cryptography is not just a future requirement but an urgent priority, as data encrypted today could be vulnerable to decryption by quantum computers in the coming decades. Governments and security agencies must prepare for this eventuality by adopting quantum-safe encryption strategies, ensuring the long-term protection of sensitive data.
Quantum Encryption
Quantum encryption, particularly through Quantum Key Distribution (QKD), is emerging as a groundbreaking technology that leverages the principles of quantum mechanics to provide theoretically unbreakable encryption. QKD allows two parties to share encryption keys securely by transmitting them via entangled particles, such as photons. The unique property of quantum entanglement ensures that any attempt to intercept or measure the quantum state of one of the particles will disrupt the entanglement, alerting the communicating parties to the intrusion.
However, while quantum encryption offers unprecedented security, it is not without challenges. Recent reports suggest that even quantum encryption systems are not entirely immune to hacking attempts. For example, there has been progress in the development of advanced computational techniques capable of deciphering quantum-encrypted communications. In particular, quantum transmission systems – once thought to be invulnerable – have demonstrated vulnerabilities when subjected to powerful enough computational resources [12].
Despite these challenges, quantum encryption remains one of the most promising solutions for securing government communications and military data against future threats, particularly as traditional encryption methods become increasingly vulnerable in the age of quantum computing. The ongoing development of quantum cryptographic systems and their implementation in strategic military and government networks will be crucial to ensuring the future security of sensitive information.
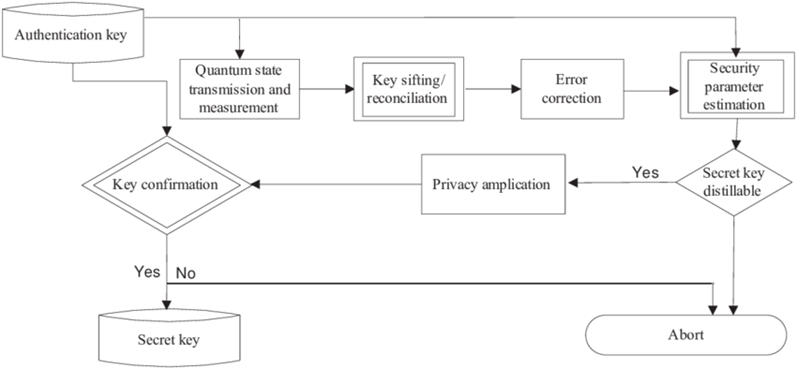
Fig. 2. Flow chart of the stages of a quantum key distribution protocol. Stages with double lines require classical authentication [12]
Homomorphic Encryption
Fully homomorphic encryption (FHE) represents a revolutionary advancement in cryptographic technologies, allowing for secure computation on encrypted data without the need for decryption. Unlike traditional encryption, where data must be decrypted before any operations can be performed, FHE enables tasks such as data processing, machine learning, and even sensitive financial transactions to be carried out securely while the data remains encrypted. This opens up a wide range of practical applications, particularly in cloud computing, where privacy concerns often limit the scope of services.
FHE relies on the mathematical complexity of discrete logarithms and factoring problems, which provide a strong foundation for its security. Although homomorphic encryption is relatively new compared to established methods like RSA and ECC, significant progress has been made in recent years. Cryptographic applications of FHE include secure voting systems, privacy-preserving medical research, and data outsourcing in cloud environments, where sensitive data must remain confidential throughout its lifecycle.
However, despite its promise, the current implementations of fully homomorphic encryption face limitations related to computational efficiency and storage space requirements. FHE operations tend to be computationally expensive, requiring more processing power and time than traditional encryption methods. Additionally, the space occupied by the encrypted data after performing homomorphic operations is often significantly larger, reducing the practicality of the method in real-world applications [13].
Nevertheless, ongoing research is focused on improving the efficiency of FHE, making it more suitable for large-scale applications like big data analytics and IoT data processing. As the technology matures, fully homomorphic encryption has the potential to transform the way sensitive data is handled, enabling secure and private computations without sacrificing performance.
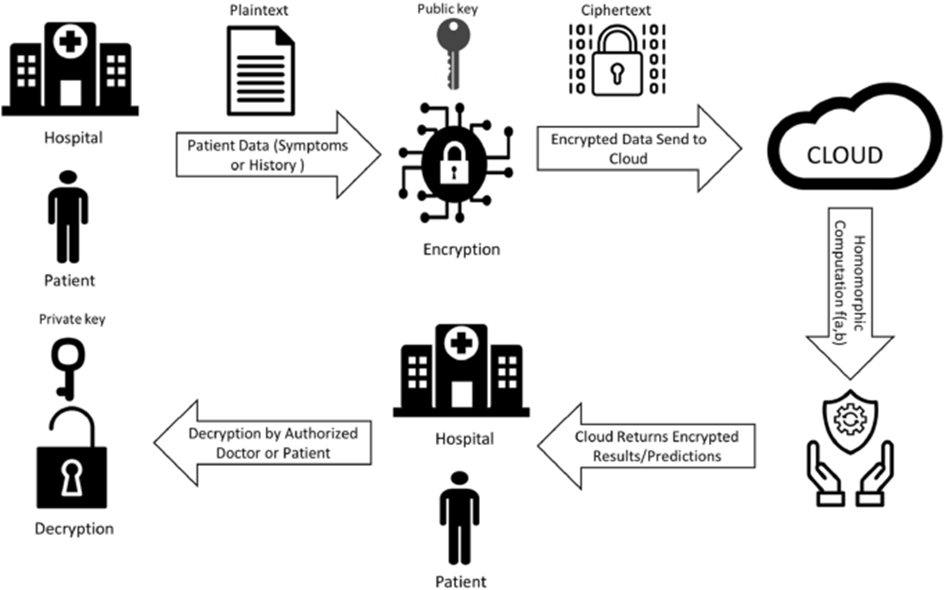 Fig. 3. Homomorphic encryption in healthcare [13]
Fig. 3. Homomorphic encryption in healthcare [13]
Concerns and Trade-offs
The implementation of cryptography and encryption in high-security environments, such as government or military networks, involves a number of important trade-offs. One major concern arises when these networks are shared with organizations in other sectors, such as hospitals or critical national infrastructure. The risk of compromising sensitive data increases when different systems, with varying security standards, are integrated into a single network. This lack of uniformity can lead to potential vulnerabilities that might not be fully evaluated, putting critical infrastructure at risk.
Furthermore, the potential for increased hostilities through the use of digital networks – whether through cyber espionage, hacking, or malicious payloads – emphasizes the need for careful consideration of encryption technologies. In high-threat environments, specific security requirements must be met to ensure secure communications. One such requirement is minimizing the encryption process by avoiding unnecessary encryption of traffic that could later be decrypted on compromised systems. This minimalist approach helps mitigate the risk of exposing sensitive information if systems are breached [8].
Another challenge lies in the management of small clusters of trusted systems over extended periods. These clusters must be tightly controlled, but this can be difficult for authorities to maintain, especially in a fast-evolving digital landscape. Finally, while signals intelligence – the collection of information by intercepting signals – will inevitably continue, it is likely to focus on locations and subjects that are of interest to intelligence agencies. As a result, commercially sensitive information may become a target, expanding the scope of what needs protection. Thus, organizations and governments need to assess not just the cryptography in use, but the broader implications of data flow and potential attack vectors within their network environments.
Future Directions and Innovations in Encryption
The landscape of encryption technology is rapidly evolving to address new challenges posed by the increasing complexity of communication channels and the growing number of connected devices. A key trend in this evolution is the development of cryptographic techniques that safeguard data as it is transmitted over unreliable communication channels. This trend is driven by the need to secure the growing amount of traffic in these channels, particularly in the context of Internet of Things (IoT) devices, which often operate in less secure environments and contribute to the complexity of data flow.
New network infrastructure protocols and encryption systems are being developed to meet these challenges. The next generation of encryption technologies focuses on unified security subsystems that can integrate cryptographic methods into the full lifecycle of data protection, from transmission to storage. These security subsystems will ensure that encryption is applied consistently across all levels of an organization, forming an end-to-end protection framework. For example, security modules could be embedded not only in database administrators' systems but also in accounting systems and across organizational departments. This would enable a comprehensive, organization-wide encryption policy that can handle higher-level security requirements and adapt to the unique needs of different departments [9].
The development of unified security subsystems will require the creation of a comprehensive security framework, taking into account the full scope of the information that needs protection. This framework must address all potential vulnerabilities, including those arising from data transmission, user access points, and data storage. It is essential to develop robust cryptographic methods that can operate efficiently across all layers of security, ensuring that data remains protected even in the face of increasingly sophisticated attacks.
Conclusion
Evaluating current encryption and data protection methods in government information systems involves an assessment of international standards, such as the Federal Information Processing Standards (FIPS) and the NIST SP 800 series [6]. These standards are widely recognized for their comprehensive guidelines on securing personal and governmental data. In particular, the NIST SP 800 series frequently provides essential recommendations for personal data security, making it a cornerstone of modern data protection practices [9].
The research analyzed over 40 encryption methods and 60 international standards and recommendations, offering a detailed review of how encryption technologies are currently applied. These findings can be used to improve existing data protection systems and evaluate the effectiveness of emerging cryptographic algorithms. For specialists with a technical background, the detailed explanations of encryption methods provided in this study will serve as a valuable resource for further development in this field.
The study focused on the modern methods used to protect government information and telecommunications systems, with an emphasis on advancements made in cryptographic techniques over the last five years. The dissemination of these findings and recommendations will be crucial to the continued evolution of cryptographic protection methods. In particular, the study highlights the need for further research in emerging areas such as quantum encryption and homomorphic encryption, both of which present significant opportunities for improving the security of sensitive information.
In addition, the current state of cryptographic protection methods was assessed, along with potential vulnerabilities in government systems. The study emphasizes the importance of updating cryptographic standards to address these vulnerabilities, especially in the context of the rapid evolution of technology and cyber threats.
In Russia, for instance, the Federal Security Service (FSB) regulates cryptographic protection services, overseeing the certification and evaluation of encryption tools. This includes conducting state tests on cryptographic devices, ensuring that these tools meet stringent security requirements, and certifying specialists responsible for managing sensitive information. As the regulatory framework continues to evolve, governments must ensure that cryptographic tools and services are aligned with the latest advancements in the field, providing a robust defense against emerging cyber threats.
The study concludes that while significant progress has been made in the field of cryptography, ongoing innovation is necessary to meet the growing demands for data security. Future research should focus on refining cryptographic algorithms, improving key management systems, and developing new approaches to secure data transmission and storage in an increasingly digital world.

.png&w=640&q=75)